7.9. Analysis Report Analysis Procedure
7.9.1. Introduction
Important
The SCORE field only makes sense for the pre-selected engine. It does not indicate that the scanned file is healthy but only that it is declared healthy by this engine.
To send the file to be analyzed to the remote server (such as the GBox) and retrieve the report, see Send file for external analysis to GCenter.
7.9.2. Prerequisites
User : member of Operator group
7.9.3. Opérations préliminaires
Login to GCenter via a browser (see Connection to the GCenter web interface via a web browser)
7.9.4. Procedure to analyse the `Error` Status
The `Error` status is indicated in part (9).
- Look at the reason for the error in the detailed text below.In this example, the error is on the Gmalcore engine which is unavailable.Here, the analysis is not significant.
Restart the Gmalcore engine on the GBox before restarting the analysis.
7.9.5. Procedure to analyse the `Clean` status
View the report.
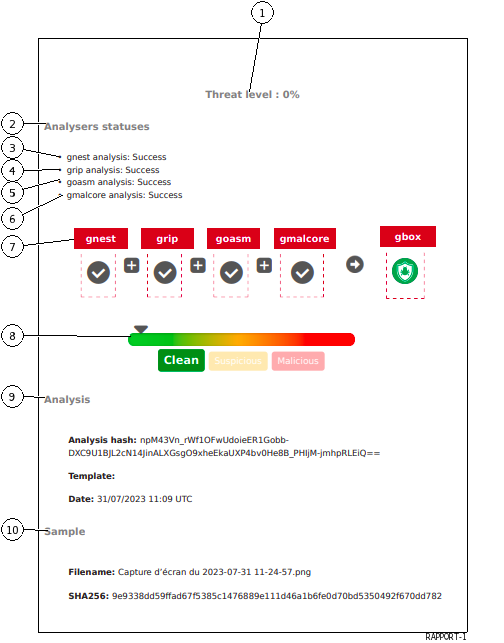 The "Clean" status is indicated in the visual signage (8).This report is composed of:
The "Clean" status is indicated in the visual signage (8).This report is composed of:
`Threat level`: here 0%This score is calculated from the analysis score returned by the different engines active of the GBox in the model at the time of detection`Analysers statuses`.This part lists the engines activated during the analysis and their results.This part indicates which analysis was done but in no case the result of the analysis:
`gnest analysis: Success`: Gnest engine analysis (3) was carried out
`grip analysis: Success`: Grip engine analysis (4) has been done
`goasm analysis: Success`: Goasm engine analysis (5) has been done
`gmalcore analysis: Success`: analysis of the Gmalcore engine (6) has been carried outThe summary of the analysis steps (7) which displays:
Part (9)
`Analysis`provides analysis information: hash, model and datePart (10)
`Sample`gives sample information: filename and sha256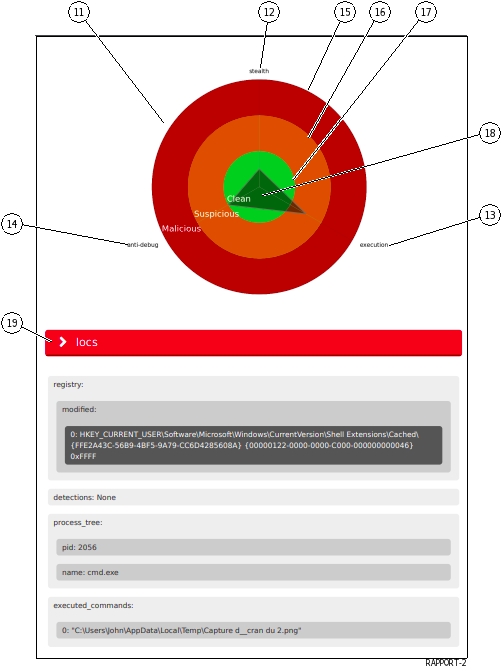
Note
Graph (11) is only available if Gnest is part of the model (the data needed for the graph is returned by this engine).
This graph (11) provides a visual on the dangerousness of the analyzed file:
The category of dangerousness is defined by axes (12) (13) and (14): titles and number of axes are given by the motors.
The level of dangerousness is given by concentric circles.
The central circle (17) indicates the healthy level.
Middle circle (16) indicates suspicious level.
Outer circle (15) indicates malicious level.
The synthesis for the file is read on the vertices of the represented form (18).In the displayed example, the vertex (5) indicates that the file is:
Suspicious in line
`execution`(13)Healthy in axis
`stealth`(12) and axis`antidebug`(14)Then the report details the parts retailers analyses: Iocs (19), Static etc..The details of these parts are given in the table below:
Part Title
Description
Is engine activated
`Analysis options`Option values used for analysis
Grip and Gnest
`Iocs`List of actions performed (files, registry, network, processes...)
GNEST
`Ttps`GNEST
`Static`Métadonnées
GRIP
`Overview`File information (size, different hash, type...)
GNEST
`Heuristic`List of engines (Entry#x) and name of the threat returned by the Gmalcore module (or n/a)
Gmalcore
`Shellcode`Result of shellcode detection
GOASM
`Signatures`List of yara signatures corresponding to the analyzed file
Gnest
`Process Tree`Graphical representation of the process tree
Gnest
7.9.6. Procedure to analyse the `Malicious` status
- Read the report.The
`Malicious`status is indicated in the visual signalétique (5).
This report is composed of:
`Threat level`: here 100%This score is calculated from the analysis score returned by the different engines active of the GBox in the model at the time of detection`Analysers statuses`This part lists the engines activated during the analysis and their results.This part indicates which analysis was done but, in no case, the result of the analysis:
`gmalcore analysis: Success`: analysis of the Gmalcore engine (3) has been carried out;The summary of the analysis steps (4) which displays:
`Malicious`Part (6)
`Analysis`provides analysis information: hash, model and datePart (7)
`Sample`gives sample information: filename and sha256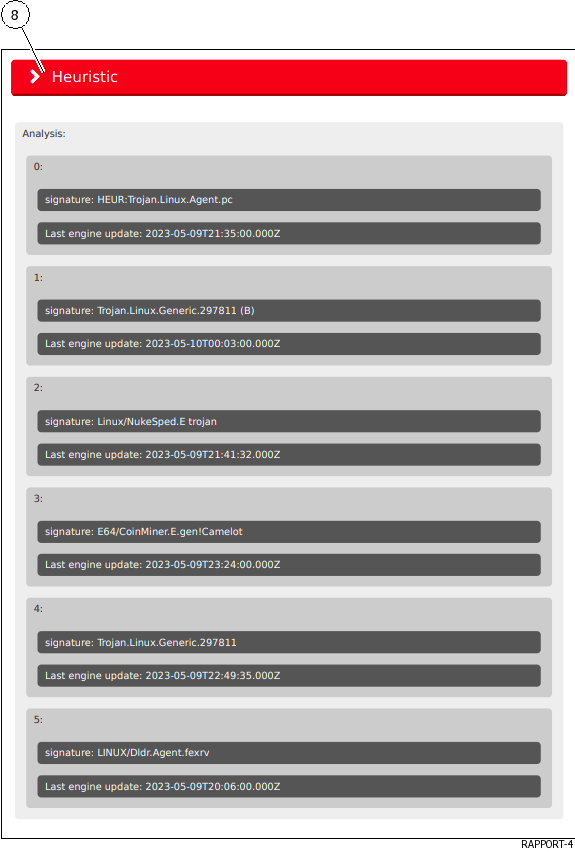 Then the detailed report the parties retailers the analyses: Heuristic (8).The details of these parts are given in the table below:
Then the detailed report the parties retailers the analyses: Heuristic (8).The details of these parts are given in the table below:
Part Title
Description
Is engine activated
`Analysis options`Option values used for analysis
Grip and Gnest
`Iocs`List of actions performed (files, registry, network, processes...)
GNEST
`Ttps`GNEST
`Static`Métadonnées
GRIP
`Overview`File information (size, different hash, type...)
GNEST
`Heuristic`List of engines (Entry#x) and name of the threat returned by the Gmalcore module (or n/a)
Gmalcore
`Shellcode`Result of shellcode detection
GOASM
`Signatures`List of yara signatures corresponding to the analyzed file
Gnest
`Process Tree`Graphical representation of the process tree
Gnest
Analyze the results according to the score.
Astuce
A non-zero score is an indication of a threat.A zero score only means that the current engine has not detected any threats.Do not hesitate to restart the analysis with all the engines of the GBox.
Concatenate the GCenter and GBox report results.