5.3. Overview of the Kibana GUI
Come from analyses on the GCap side (alerts and metadata reported by the Sigflow detection engine)
Come from analyses on the GCenter side (malware, shellcode, powershell, retrohunt or machine learning alerts)
Important
This section describes the graphic elements accessible to members of the operator group.
5.3.1. Configuration of the Kibana GUI
Users who are members of the group operator can view the data present in the detection event dashboards
Users who are members of the group administrator can view the data present in the system dashboards (Syslog)
Note
Kibana interface access is available:
For members of the operator group, by clicking on the
`Hunting`button on the navigation barFor members of the administrator group, by clicking on the command
`GCenter/Trackwatch logs`from the menu`Admin`
5.3.2. Native dashboards
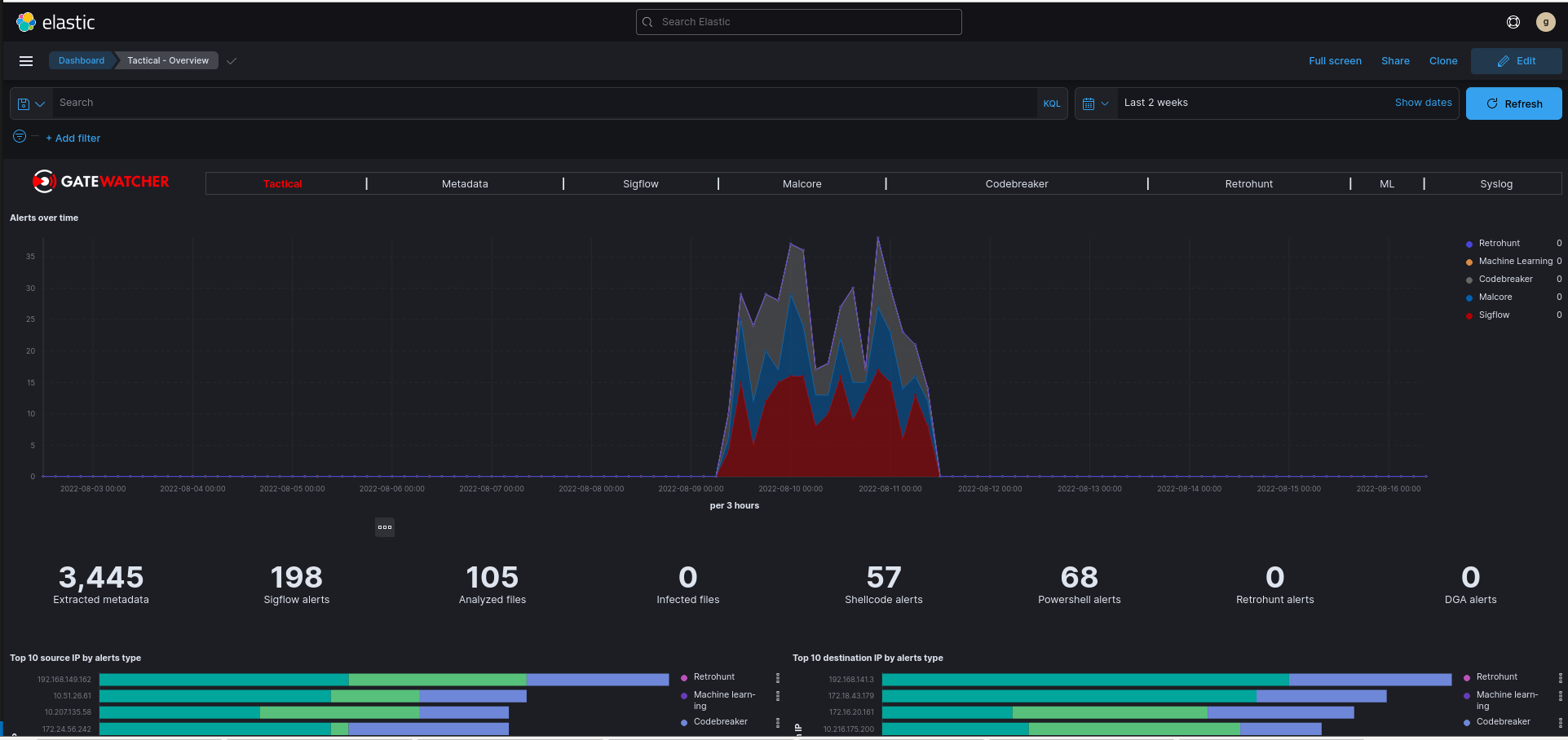
The native dashboards are grouped in the Kibana interface as tabs:
`Tactical`Metadata``Sigflow``Malcore`Codebreaker``Retrohunt`ML`Syslog`
Note
For most dashboards, three pages are available:
`Overview`
`Messages`
`GeoIP`
`Tactical`displays, in visualizations, the alert information of the different engines:
a graph showing the number of alerts per engine over time
a counter displaying the number of alerts per engine, the number of metadata and the number of files scanned
a top 10 source IP addresses by type of alert
a top 10 destination IP addresses by type of alert
a graph showing the proportion of the different severity of Sigflow alerts
a graph showing the number of unique signatures that escalated alerts over time
a list of Malcore alerts identified by the solution (in the form of a message)
a top 10 Codebreaker alerts
a top 10 Retrohunt alerts
a top in the distribution of DGA domain names (Machine Learning)
Top 10 Machine Learning Alerts
`Metadata`displays, in sub-tabs, the metadata for the different protocols analyzed by the probe:
All, synthesizes all metadata into visualizations in chart form
DHCP, DHCP metadata details
DNS, DNS metadata details
File Transaction, details of the metadata related to the file reconstructed by the probe
HTTP, HTTP metadata details
IKEv2, IKEv2 metadata details
KRB5, KRB5 metadata details
NFS, NFS protocol metadata details
SMB, SMB metadata details
SMTP, SMTP metadata details
SSH, SSH metadata details
TFTP, TFTP metadata details
TLS, TLS metadata details
Attention
Some protocols do not have a native dashboard despite the fact that they can generate metadata.These metadata are still indexed and usable in Kibana.
`Sigflow`displays all alerts generated by Sigflow`Malcore`displays all malware alerts generated by the Malcore engine`Codebreaker`displays all shellcode and powershell alerts generated by the Codebreaker engine`Retrohunt`displays all alerts generated by the Retrohunt engine`MetaMLdata`displays all alerts generated by the Machine Learning engine;`Syslog`displays the solution’s syslog system events (accessible only by administrators)
5.3.3. Data exploitation
Filter by changing the time interval (top right of page)
Filter by searching using the
`Search`bar (top left)Filter by creating a filter on a specific field of the desired events (button
`+ Add filter`below the search bar)