1.5. Overview of the GBox
automatically receiving suspicious files requiring in-depth malware analysis, without having to rely on an external service
Analysing suspicious files on demand from the GCenter's Web UI interface
sending reports back to the GCenter for files submitted to it that are visible from the GCenter's Web UI and from the GBox's Web UI
Analysing files directly on the GBox Web UI and generating a corresponding report
users to manually analyse domain names that were generated by the Domain Generation Algorithm (DGA).
1.5.1. Server templates
For more information, please refer to the Mechanical characteristics section.
1.5.2. List of the GBox inputs / outputs
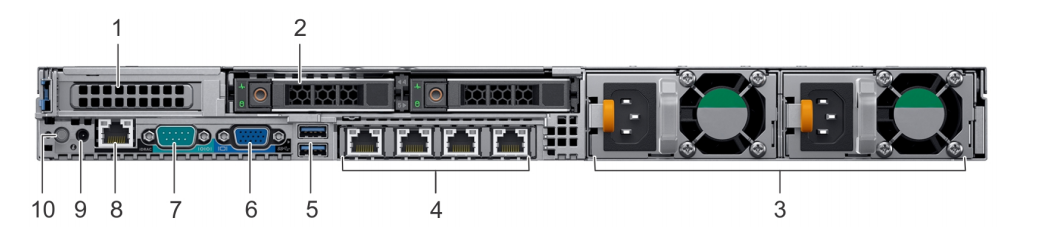
The GBox comprises:
Item |
Name |
|---|---|
4 |
RJ-45 connector
`GBX0`: management interface and link with the GCenter .RJ-45 connector
`GBX1`: interface dedicated to Virtual Machines for Internet access, Gnest VMs can be accessed via this link.RJ-45 connector
`GBX2`: Not usedRJ-45 connector
`GBX3`: Not used |
5 |
USB connector: accommodates the USB key enabling disk decryption (standard Linux Unified Key Setup)
USB connector: direct access via keyboard
This connection mode is deprecated in favour of KVM/IDRAC/XCC and should only be used as a last resort.
|
6 |
VGA connector: direct access with a screen.
This connection mode is deprecated in favour of KVM/IDRAC/XCC and should only be used as a last resort.
|
Note
Connector details can be found in the Dell EMC PowerEdge R640 Installation and Service Manual.
1.5.2.1. Use of USB and VGA connectors
Connecting a keyboard and monitor enables direct access to the GCenter console interface.
Important
1.5.2.2. Access to the server's management and configuration interface
Access to this management interface is via HTTPS:
On a Dell server, this connector is called iDRAC. It is noted on the KVM/IDRAC diagram
On a Lenovo server, this connector is called TSM: This connector can be identified by a wrench symbol on the bottom of it.
1.5.2.3. Interface network `Gbx0`
This interface enables remote administration using the SSH protocol to access:
The installation/configuration menu
The Web user/administration interface
This interface also serves to send files to be analysed from the GCenter to the GBox.