This part of the GCENTER enables the management of users and associated groups, the history of authentications on the platform, and also the association with a Lightweight Directory Access Protocol (LDAP) server.
From this configuration interface, the administrator will be able to customise the parameters of the GCENTER management solution via these five tabs:
[Users management](#local user)
1. Local users

Menu: Administrators > GCenter > Accounts > User management
From the user account configuration menu of the TRACKWATCH solution, it is possible to create user accounts each having different rights. The proposed groups fully comply with the Military Programming Law.
The creation of a user and the associated profile can be configured from this view. Indeed, depending on the commands or actions carried out, it will be necessary to belong to a given group.
Within this documentation, the details of the group allowed to perform the action are specified in each section by the  and
and  badges respectively. This is the case if Administrator rights are required or if Operator rights are required.
badges respectively. This is the case if Administrator rights are required or if Operator rights are required.
The administrator fills in the name/first name/email/password of the user to be created. These completed fields will then be used to trace the user in the history if changes are made.
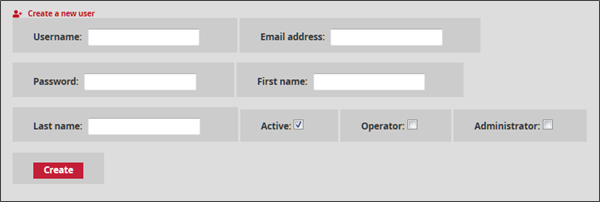
Username is the field to be filled in by the administrator to enter the full name of the new user of the GCENTER management platform. This value can only contain letters, numbers and characters [@/./+/-/-/_.].
First name, Last name, and Email address are optional fields upon user creation. They provide information on the profile's first name, last name, and email address respectively.
Password is for the user's password for the created account. This password must contain a minimum of seven characters.
Operator and Administrator** represent groups. Once the box is ticked, the user will have the appropriate permissions for the selected group.
Active: Enables/disables the user account.
The Operator group will be able to: add or delete detection rules, view generated alert logs, scan files, view the Smartmap, and have an overview of the Suricata signatures in the Sigflow area.
The Administrator group will be able to: update the operating system, software, reboot the equipment, edit and view the network configuration, update the detection interfaces, view the version, attributes, add or delete a probe. The Administrator group can enable or disable the sending of additional technical information to operators, enable or disable the storage of additional technical information while defining the duration, and consult all the operating and alert logs generated.
Any of this information can be taken into account after the administrator saves the changes by pressing Create.
Below is a list of all the users created by the system administrator with the information related to each profile ('Enabled' being the status of the profile, activated or deactivated):
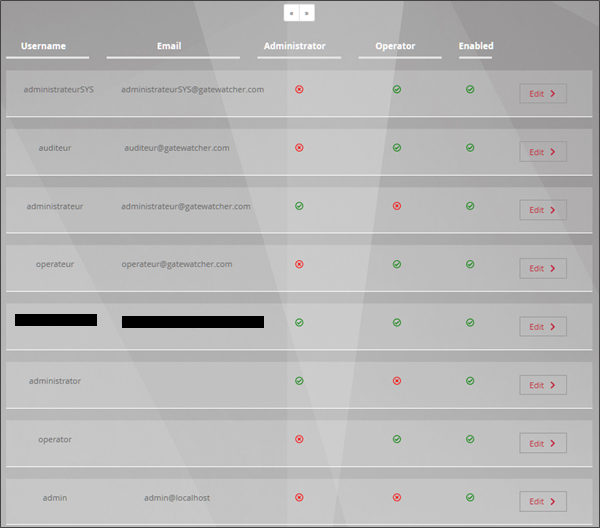
The Edit button will be used to modify the user profile in question. Various permissions are possible for a user depending on the group membership. It is possible to decide to assign administrative rights to a user according to their scope of action.
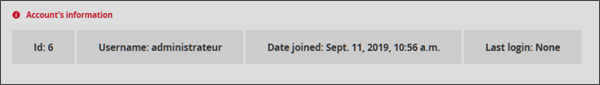
The Account's information contains the user's profile information, i.e. user ID, full name, creation date, and the last time the user logged on to the GCENTER management platform.
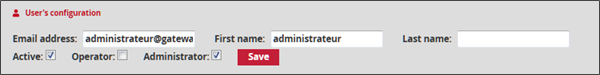
User's configuration enables modifying the email address, first and last name of the user profile. In addition, the groups created by default in accordance with the Military Programming Law appear. They may or may not be assigned to the profile by ticking the check box provided for this purpose. The administrator can enable or disable the platform user via the Active option. The consequence of this option will result in an inability to connect to the GCENTER interface.
Any modification will only be applied after pressing Save.
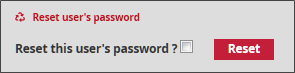
Reset user's password enables the password associated with the user account to be regenerated if it is lost or forgotten. The platform will propose a new password to log in again once the 'Reset' button is selected.
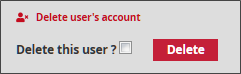
In Delete user's account , the Delete option enables the administrator to remove any user profile from the platform.
The administration interface therefore enables the rights to be fully configured at all levels of the GCENTER administration. Any creation of a user from the GCENTER will be taken into account by the GCAP probe. The user will be added to its database.
2. LDAP Integration / ActiveDirectory

Menu: Administrators > GCenter > Accounts > LDAP Configuration
The TRACKWATCH user account configuration menu enables the use of Lightweight Directory Access Protocol (LDAP) as the authentication backend rather than the internal backend.
This interface is used to manage the connection between the GCENTER and an LDAP/ActiveDirectory server.
LDAP interconnection status enables easy identification of the connection status.
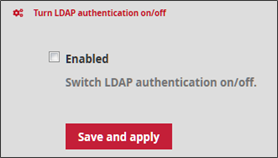
In the Turn LDAP authentication on/off section tick the Enabled box to activate the service and then click Save and apply to take the change into account.
Saving and applying the new LDAP option configuration will cause a restart of the application and therefore a disconnection from the user page.
Once the administrator clicks Confirm, it will be necessary to reconnect to the interface. Before this manipulation, the connection options to the LDAP server can be set in the LDAP server binding settings section:
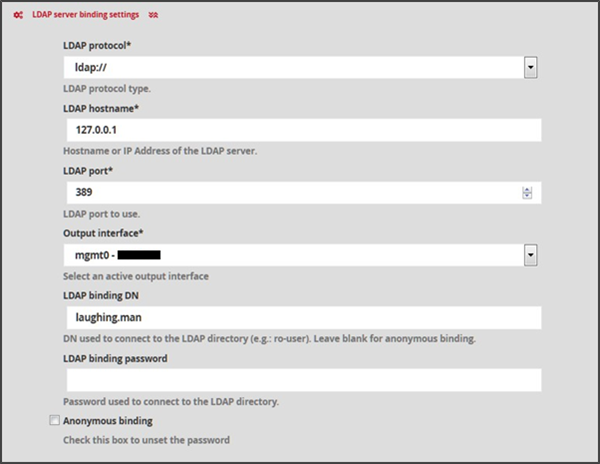
LDAP protocol: corresponds to the type of authentication protocol selected: LDAP or LDAPS
LDAP hostname: full FQDN address or IP of the LDAP/ActiveDirectory server
LDAP port: corresponds to the port number of the LDAP service. (Example: 389)
Output interface: The output interface to be used to reach the LDAP server.
LDAP binding DN: corresponds to the Distinguished Name (DN) used to connect to the LDAP directory. Leave the field empty if the connection is anonymous. (Example: CN=adro,OU=Service Accounts,OU=Example,DC=Example,DC=com,ro-user)
LDAP binding password: password used to connect to the directory. Leave the field empty if the connection is anonymous.
Anonymous binding: enables the use of a password for authentication to be disabled.
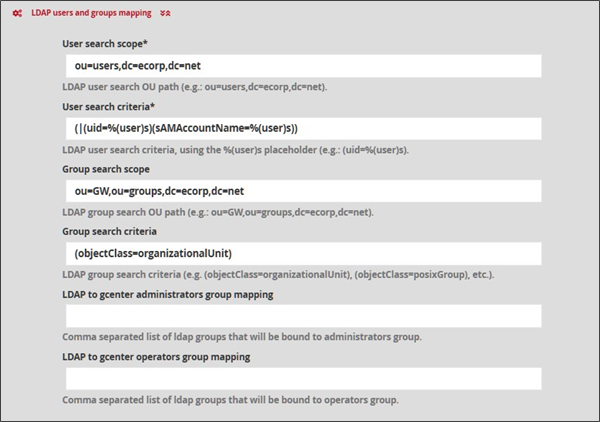
The LDAP users and groups mapping section:
User search scope: Basic OU (Organisational Unit) for user search (Example: ou=users,dc=ecorp,dc=net)
User search criteria: LDAP user search criteria, by means of the %(user) space provided (Example: (|(uid=%(user)s)(sAMAccountName=%(user)s)))
Group search scope: Basic OU (Organisational Unit) for group search (Example: ou=GW,ou=groups,dc=ecorp,dc=net)
Group search criteria: Search criteria for LDAP groups, using the %(group) space provided (Example: (objectClass=organizationalUnit))
LDAP to GCENTER administrators group mapping: is a comma-separated list of LDAP groups related to the solution's administrators group.
LDAP to GCENTER operators group mapping: is a comma-separated list of LDAP groups related to the solution operators group.
The LDAP advanced settings section enables accessing the advanced LDAP options.
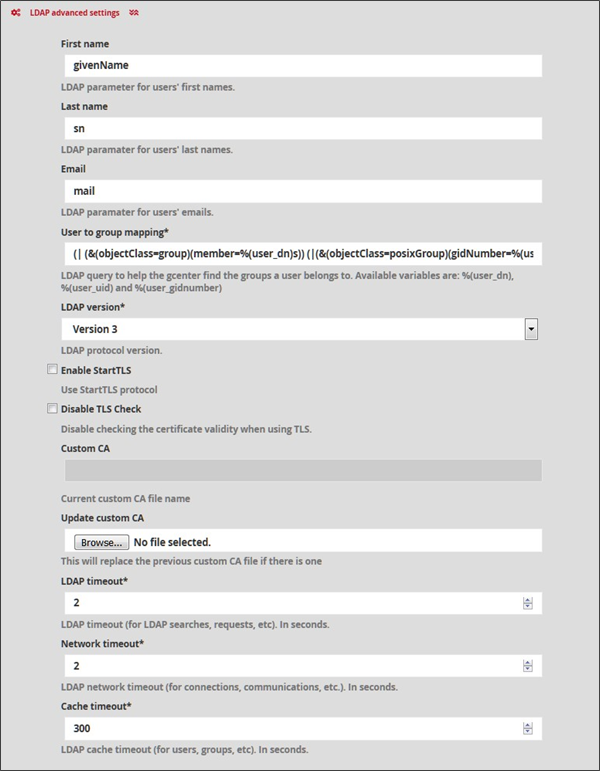
The LDAP parameters can be modified from this interface for the first name of the user, the last name, the email, the type, the version, the timeout of the service (in seconds) after each request, connection, or communication. The time before the timeout (in seconds) of the cache for users or groups is also configurable.
First name: LDAP parameter corresponding to the user's first name (Example: givenName)
Last name: LDAP parameter corresponding to the user's last name (Example: sn)
Email: LDAP parameter corresponding to the user's email address (Example: email)
User to group mapping: LDAP query to help find the groups to which a user belongs. The available variables are: %(user_dn), %(user_uid) et %(user_gidnumber)
LDAP version: version LDAP to be selected ( Version2 | Version3)
Enable StartTLS: allows activating the use of StartTLS. Disabled by default.
Disable TLS check: setting to stop checking the validity of the certificate when the TLS service is enabled.
Custom CA: Information about the customised CA used.
Update custom CA: replaces the custom CA certificate.
LDAP timeout: modifiable timeout in seconds for LDAP searches or other queries (Example: 2)
Network timeout: delay in seconds for network connections or communications (Example: 2)
Cache timeout: LDAP cache expiration time in seconds for users and groups (Example: 300)
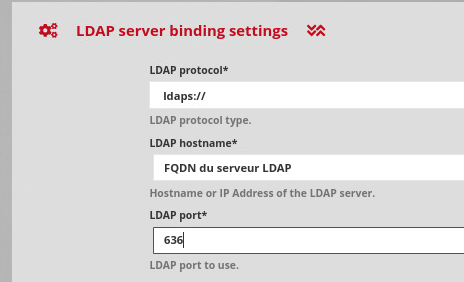
For an LDAPS configuration:
From the standard LDAP configuration explained above, it is necessary to:
Enter in "LDAP server binding settings":
LDAP protocol:ldaps://LDAP_port:636
Enter the certificate of the certification authority in "LDAP advanced settings".
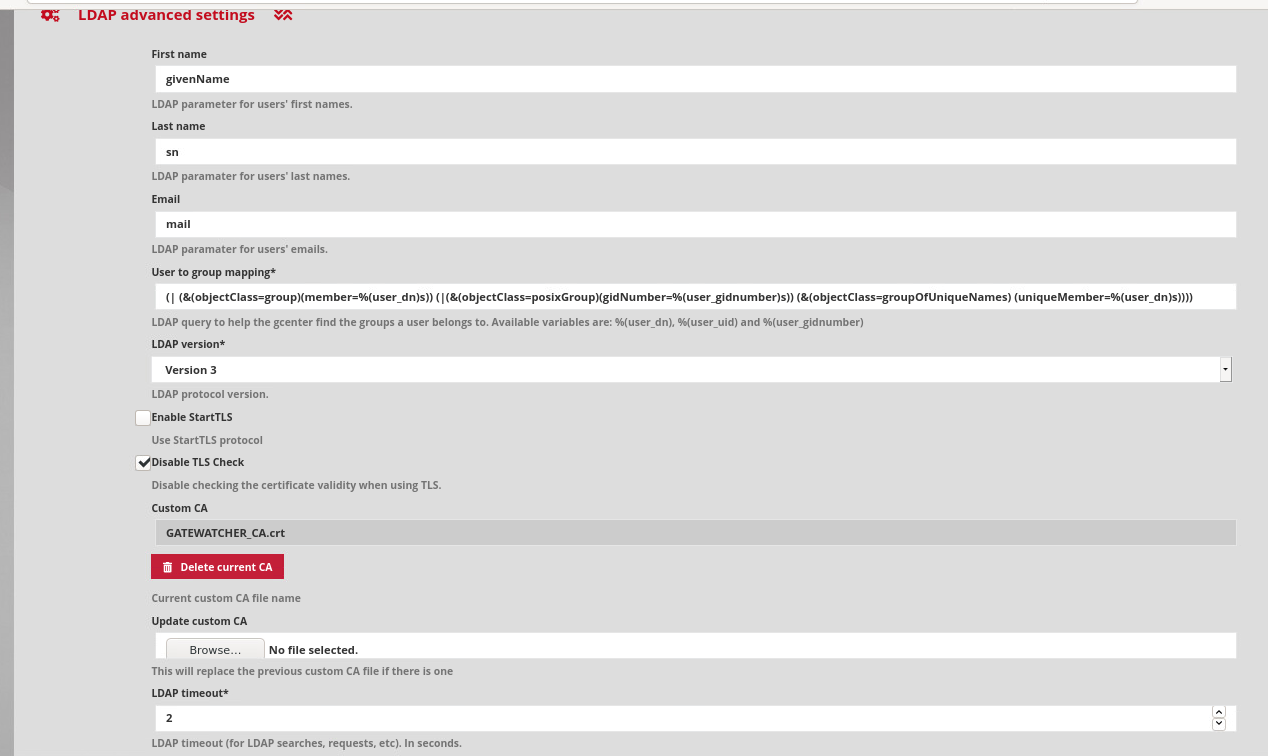
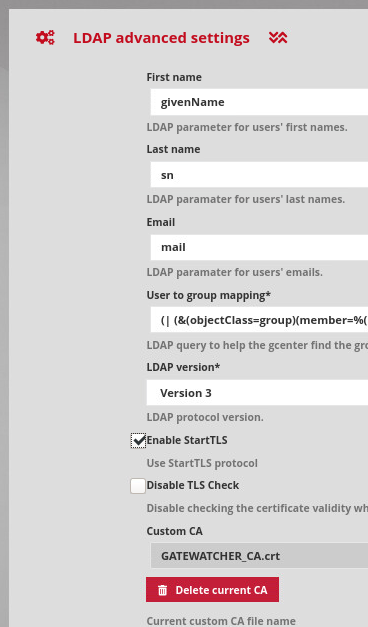
For an LDAP over TLS configuration:
From the standard LDAP configuration explained above, it is necessary to:
Fill in the certificate of the certification authority in "LDAP advanced settings".
Tick the "Enable StartTLS" box in "LDAP advanced settings".
3. Audit trail

Menu: Administrators > GCenter > Accounts
The TRACKWATCH solution will record the various actions carried out on the human–computer interaction (HCI) linked to user management on the management platform over time, in order to ensure traceability. This traceability is carried out both for the connection of users and for the creation/deletion or modification of permissions.
3.1. Authentications history

Menu: Administrators > GCenter > Accounts > Authentications history
 The history of all authentications on the GCENTER is available.
The history of all authentications on the GCENTER is available.
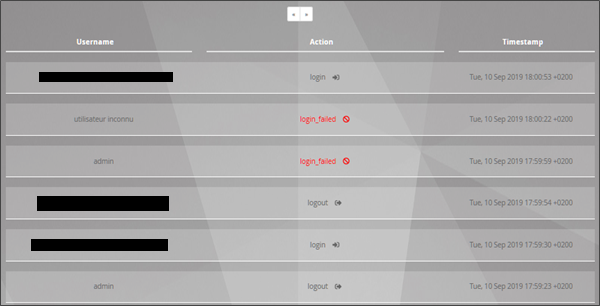
A connection history of the user logins on the platform is present in the form of a timestamp in the format [day, xx month year hh: mm: ss].
3.1.1. Creations/Deletions history

Menu: Administrators > GCenter > Accounts > Creation/Deletion history
 The history of all creations or deletions of GCENTER users is available. All the modifications made by an administrator account of the system on a user can be found at this level.
The history of all creations or deletions of GCENTER users is available. All the modifications made by an administrator account of the system on a user can be found at this level.

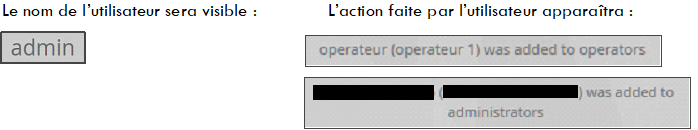
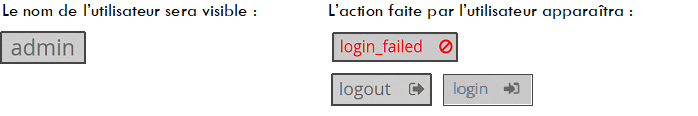
In the Username column, the administrator's name responsible for adding or deleting the user is visible.
The Log message column contains information such as the user's name and the action associated with the account (created or deleted).
A history of user logins created and deleted on the platform is present in the form of a Timestamp in the format [day , xx month year hh: mm: ss].
3.1.2. Permissions history

Menu: Administrators > GCenter > Accounts > Permission history
 The history of all user permissions on the GCENTER is available. All changes to the rights on a profile are visible via this page.
The history of all user permissions on the GCENTER is available. All changes to the rights on a profile are visible via this page.

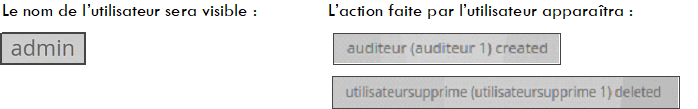
In the Username column, the administrator's name responsible for modifying the user's group is visible. Note that belonging to a particular group results in changes to the rights of the user profile on the platform.
In Log message, we find several pieces of information such as the name of the user and the action associated with the account (was added to...).
A history of the allocation of rights on the platform's user logins is present as a timestamp in the format [day**, ** xx month year hh**: mm: ss].