1. MISP (Malware Information Sharing Platform)

Menu: Administrators > GCenter > Third-Party Modules > MISP
This interface is used to manage the connection between the GCENTER and a Malware Information Sharing Platform (MISP) server already present in your infrastructure.
 Connecting an MISP server to the TRACKWATCH solution enables the provision of technical threat information as well as a repository of malware, Indicators of Compromise (IOC) and information.
Connecting an MISP server to the TRACKWATCH solution enables the provision of technical threat information as well as a repository of malware, Indicators of Compromise (IOC) and information.
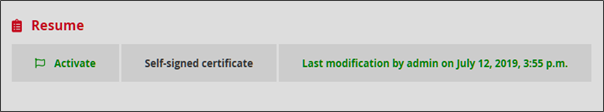
From the MISP Suricata rules section, the administrator can view the most recent configuration change of the MISP instance and make changes by clicking Access.

The administrator can check the connection status between the MISP instance and the GCENTER via Resume.
Once in Access, the first step is to specify the IP address or domain of your MISP instance in the GCENTER WebUI.

Protocol: the communication protocol to apply to contact the MISP instance. Two options are possible: 'HTTPS' and 'HTTP'. MISP instance IP or FQDN: The domain name or IP address of the MISP instance. MISP access port is the listening port of the MISP instance. Output interface is the physical interface of the GCENTER through which it will communicate with the MISP server. MISP API key the administrator enters the API key of the MISP instance.
Once the section is completed, simply click on 'Save' to record the information.
The MISP connector enables IOCs to be sent directly from a local MISP to the GATEWATCHER probes. This connector enables adding a quality threat intelligence source, while respecting the ANSSI guidelines on signature qualification.
Now that the service is activated, it can be seen that the MISP interconnection status has been modified. The link between the GCENTER and the MISP instance is operational.
2. Hurukai (by HarfangLab)


Menu: Administrators > GCenter > Third-Party Modules > Hurukai
HarfangLab offers an Endpoint Detection Investigation and Remediation (EDiR) or EDR solution known as Hurukai. This solution enables investigating cyber-attacks without slowing down the company's operations. Hurukai will enable real-time collection of information on endpoints through the use of agents that will be deployed by the solution's management server. The agents are compatible with Windows 7, 8, 8.1, 10, and Windows server 2008, 2012, and 2016 platforms.
The purpose of this section is to connect the GCENTER to the Hurukai EDiR via the "Third Party modules" section in the GCENTER administration. Then simply move to the "Hurukai" tab to access the function.
To interconnect the two devices, simply enter the IP address or URL and the associated Hurukai communication port in the appropriate fields:
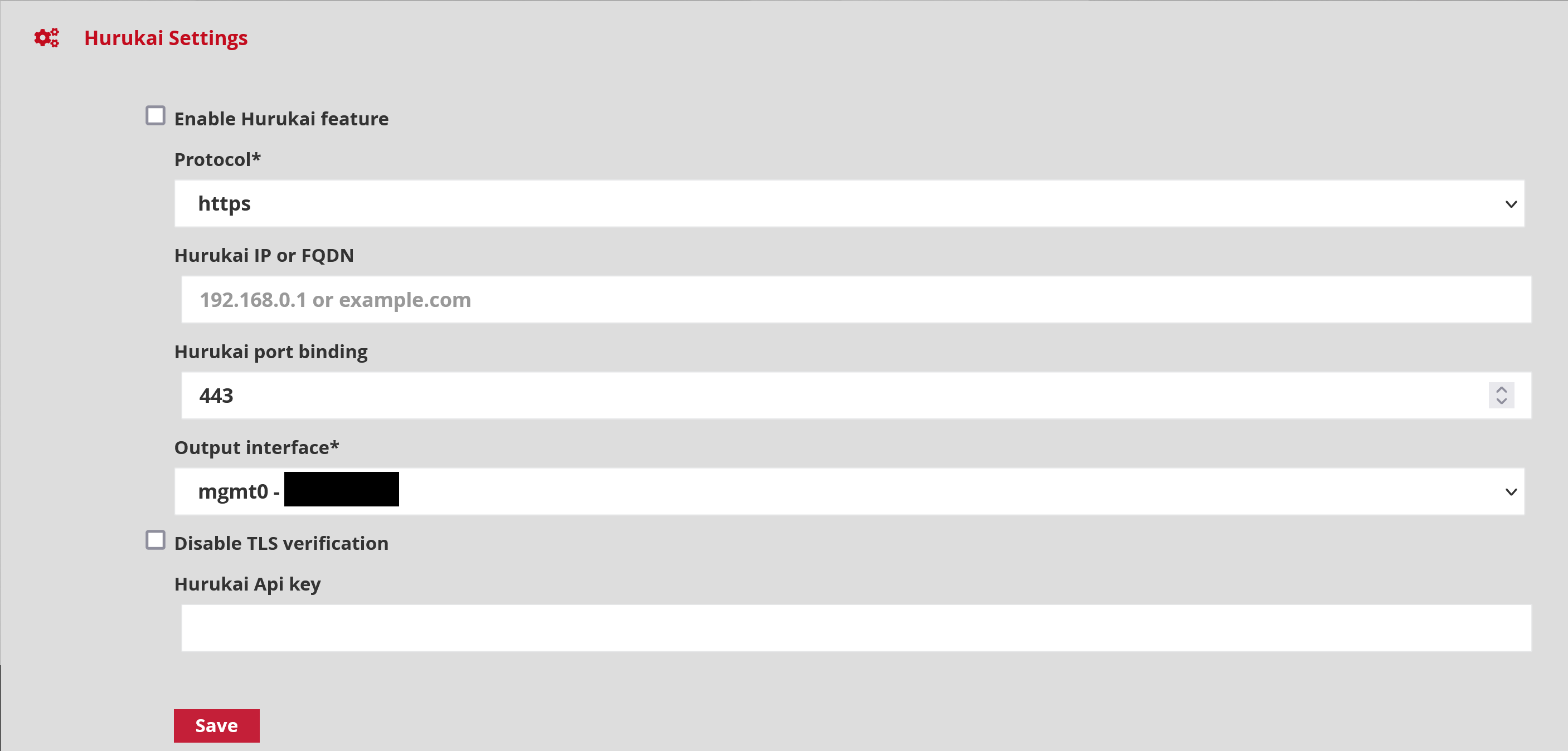
Protocol communication protocol to apply to contact the MISP instance. Two options are possible: 'HTTPS' and 'HTTP'. Hurukai IP or FQDN: the domain name or IP address of the Hurukai instance Hurukai port binding: the listening port of the Hurukai server Output interface: is the physical interface of the GCENTER through which it will communicate with the Hurukai server. Hurukai API key: is the Hurukai API key.
Once the section is completed, simply click on 'Save' to record the information.
The EDiR search engine instantly identifies anomalies, generating alerts through suspicion-raising functions. Markers of known attacks, attacker tools, bootkits, the presence of unsigned code, and injected code will be identified.
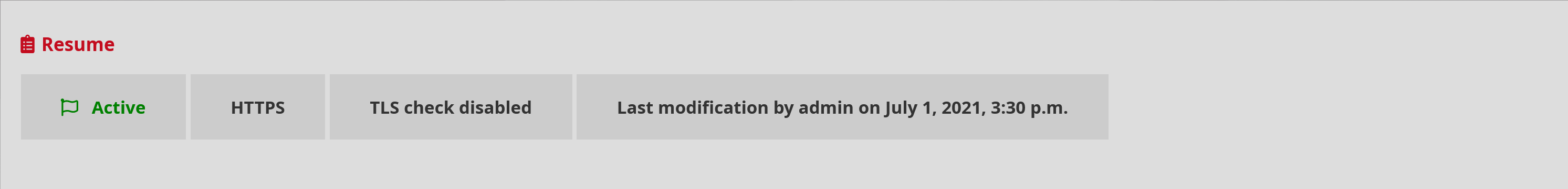
The service is now activated and functional.