1. MPL: reminders
Some reminders of the main principles of the MPL:
Military Programming Law
Act no. 2013-1168 of 18 December 2013
Article 22: implementation supervised by the ANSSI for the OIVs
Impose security measures,
Impose controls on the most critical information systems
Make it compulsory to report incidents observed by OIVs on their information systems
Article L.1332-6-1 of the Defence Code amended by Act no. 2015-917 of 28 July 2015 - Art. 27
Establish organisational and technical measures
Define procedures for identifying and reporting security incidents affecting vital information systems (SIIV)
The objectives are to protect national critical infrastructures against cyber attacks, reduce exposure to risks, and optimise the quality of services provided by organisations.
Requirements for OIVs and security incident detection service provider (PDIS) actors are to be taken into account on TRACKWATCH equipment:
Implement an information systems security policy
Carry out a security certification
Communicate the elements on the IVIS set up by the operator to the ANSSI
Observe and react to security alerts.
Limit access
Partition the networks
Select the qualified technologies

2. MPL applied to GCENTER
Here we will discuss the specific configuration steps that will enable the TRACKWATCH solution to meet the requirements of the Military Programming Law.
Although a number of actions are performed automatically when entering MPL mode, the administrator will have to customise and modify some of the parameters manually:
Strengthening (GRsec, binaries, PAX and modules)
automatic actionGScan
automatic actionAD/LDAP
manual action requiredUSB port
automatic actionOffline Update - manual action required
Upgrade Hotfix
automatic actionInterface separation
manual action requiredCertificate integration
manual action requiredIDRAC Disabled
manual action requiredThe groups
manual action required
2.1. Automatic action
2.1.1. Strengthening (GRsec, binaries, PAX, and modules)
To perform a strengthening of the GCENTER and enter MPL mode, follow the procedure below by connecting to the SETUP interface:
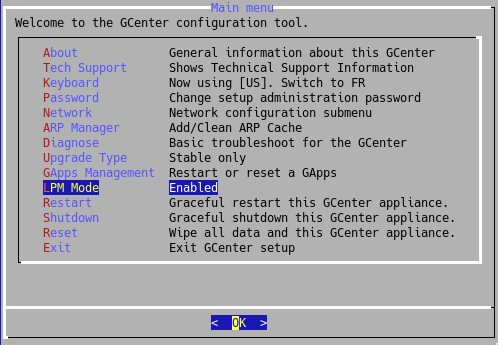
Connect via the GCENTER setup account (SSH or terminal)
Select the 'MPL Mode' tab that is disabled by default
Validate the option to switch to MPL mode
The equipment will then restart with the configuration correctly loaded.
This will enable the GCENTER to reduce its attack surface and thus reduce the risk. Indeed, by using this mode, it integrates the GRSECURITY improvements, including PaX. Enabling the attack surface to be reduced even at the core level.
2.1.2. GScan Service
In the same way, some functions are disabled. This is the case of the GScan service that is disabled for the detection of potential malware or shellcodes.
This feature automatically deactivates itself after enabling MPL mode in the SETUP.
2.1.3. USB Port
When the TRACKWATCH solution is in MPL mode, the USB ports are automatically disabled once the keyboard or other peripheral device is disconnected. The GCENTER or GCAP probe must be rebooted and the device must be reconnected prior to startup to ensure that it is supported. This limits access to the device's TTY.
The change is made automatically after switching to MPL mode from the SETUP profile settings menu.
2.1.4. Hotfix upgrade
In the context of an IS subject to the MPL, the GCENTER will not be able to apply a hotfix type of modification to the solution in order to correct minor problems on the solution without rebooting.
This GUM parameter is automatically deactivated after validation of the MPL mode in the SETUP.
However, patches can still be applied via the upgrade process.
2.2. Manual action
The following list of actions should only be performed by an administrator of the TRACKWATCH solution.
2.2.1. AD/LDAP account
In the context of an IS subject to the MPL, there are certain constraints, in particular the fact that the GCENTER is not connected to an Active Directory or LDAP. It is necessary to check whether this is the case.
To do this, go to the ADMINISTRATORS section of the GCENTER and click on Accounts and LDAP configuration.
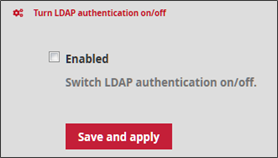
Uncheck the Enabled box and click Save and apply to apply the change. This change will cause the application to restart, resulting in a disconnection from the user page. Once the administrator clicks Confirm, it will be necessary to reconnect to the interface.
After this manipulation, a green banner validates the modification. The LDAP interconnection status section indicates that the GCENTER is now disconnected from the Active Directory or LDAP.
2.2.2. IDRAC Disabled
The TRACKWATCH solution is installed on Dell equipment. The latter offers the possibility of configuring an IP address independent of the capture environment enabling it to be remotely controlled. These connection interfaces are referred to as IDRAC by the brand manufacturer. According to the ANSSI, it is recommended they be deactivated for obvious security reasons. However, they can be reactivated at any time by the administrator to facilitate maintenance.
2.2.3. Separation of interfaces
In the context of an IS subject to the MPL, the GCENTER must have a special configuration of its network interfaces. Indeed, in order to guarantee this compliance and a good level of security, the management flow and the event flow generated by the GCAP probes must be on two different interfaces respectively [MGMT0] and [VPN0].
This change does not take effect automatically after the MPL mode is activated, even if the network cables are correctly connected. It is precisely from the SETUP interface that the administrator can make the change and manually add a new IP address for the [VPN0] interface. Only the [MGMT0] and [VPN0] interfaces are affected. Refer to the setup document in order to make the change.
Details of the flows in this mode are described in the [Flow Matrix] section (install.html#flow-matrix)
The sending of logs to a security information and event management (SIEM) in an operating zone will be done through a dedicated interface. We separate the management interface (administrator) from the log export interface (operator).
important:: In MPL mode, the [ICAP0] interface is disabled and the [SUP0] interface must be in a different network than [MGMT0].
2.2.4. Offline Update
In order for the TRACKWATCH solution to comply with the Military Programming Law, signature updates must be done in Manual or Local mode.
Therefore, there are two possibilities:
Either from the GCENTER web interface. See the [Manual Engine Update] section (update.html#manual-engine-update) of this document. This corresponds to a manual update.
Or via a location on the network, disconnected from the internet. This corresponds to a Local update (see section Local mode).
2.2.5. Certificate integration
In order to comply with the specific requirements concerning the use of cryptographic mechanisms, GATEWATCHER advises referring to the documents written by the national authority on information system security and defence.
The Military Programming Law imposes rules and recommendations concerning the management of the keys used, authentication mechanisms, and the choice and sizing of cryptographic mechanisms. All these prerequisites are available in the RGS General Security Reference (RGS B1, RGS B2, and RGS B3) of the ANSSI.
The SSL Settings section indicates how to add your own SSL configuration.
2.2.6. Groups
In order to respect the separation of roles within the TRACKWATCH solution, two profiles are available.
The system administrator performs several types of tasks. Changes to the network configuration, viewing, editing, and updating detection rules and packages.
The profile may add, delete, edit, activate, deactivate, and view information about detection rules. The system administrator will manage the creation, import, export, and destruction of cryptographic elements, consult the version, alert logs, perform system and software updates, and have user management for the creation, deletion, and modification of accounts associated with the roles. In addition to being able to modify the global parameters of the GCENTER, the administrator will also be able to stop, start, and restart the functionalities or the solution itself.
The operator can view all of the operating logs and alerts generated. In addition, the operator will also be able to activate and deactivate the storage of additional technical information while defining the duration.
The profile will be able to download the captured data, interact with the analysis and download platform if configured, scan files, observe the SmartMap and most importantly read or modify information related to the detection rules (addition, deletion, specific actions).
In the administration interface of the GCENTER, default groups are already created to facilitate managing the client's users.
Profiles are managed from the user management.