1. Presentation
The CODEBREAKER analysis engine enables:
The detection of exploitative techniques that are offensive, discrete, and sophisticated.
De-encoding of encrypted payloads.
Detection of polymorphic shellcodes.
Codebreaker addresses shellcodes for Windows and Linux platforms in 32 and 64 bits.
2. Detection
Menu: OPERATORS > Inspectra > Codebreaker
From the 'OPERATORS - Inspectra - Codebreaker' section, the operator can access a table listing encoded and unencoded shellcodes, polymorphs, and powershells through the CODEBREAKER detection engine.
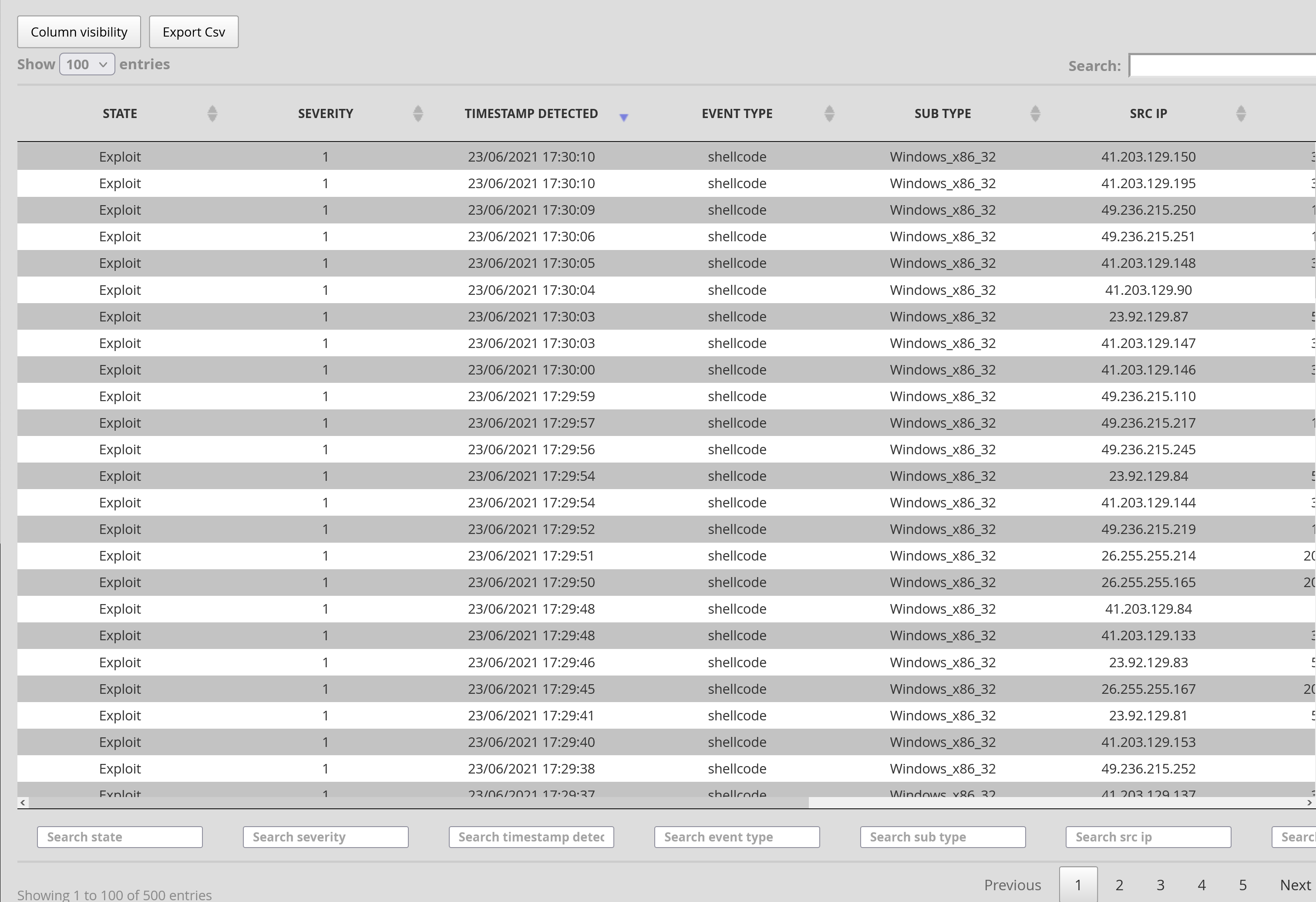
Above this table, the operator can click on the ' From - To' field to define the time range (in the format dd/mm/yyyy HH:MM) of the data being displayed.
Number of results max: is the maximum number of results displayed in the table.
The table's columns are movable and dynamic searches can be made on each of them:
The operator can choose the visibility of the columns in the table by clicking on the Column visibility button.
It is also an option to perform a quick CSV export of the data based on the selected decision date:
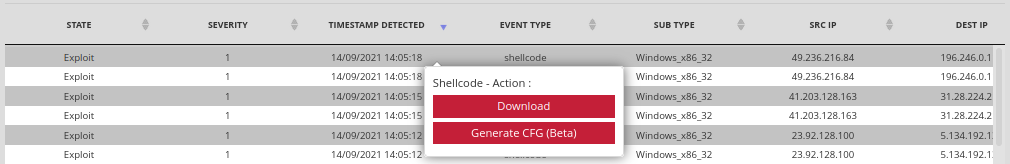
An interactive analysis of the element is possible by means of a right click of the mouse. With 'Download' it is possible to retrieve the Shellcode/PowerShell and save it on the computer in a password protected file in `.zip' format. This password can be changed here.
The operator can also run the 'Generate CFG' function to obtain a simplified, graphical version of the detected Shellcode instructions.
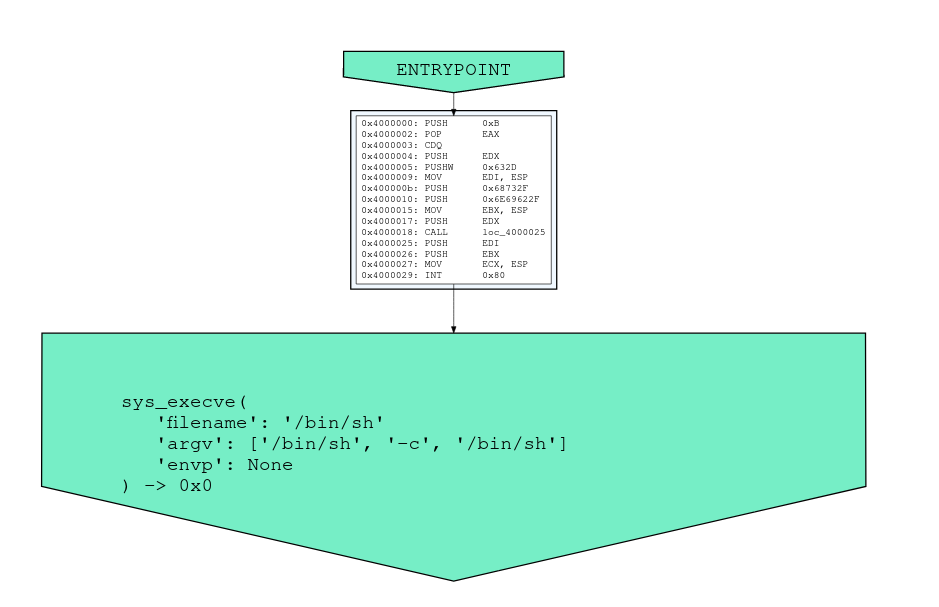
Below is an example of a CFG generation of a simple shellcode detected by the CODEBREAKER analysis engine:
Finally, as with the rest of the information analysed by the TRACKWATCH solution, the data generated by Codebreaker is available in the dedicated Kibana dashboard.
3. Generated events
3.1. Codebreaker Shellcode
3.1.1. Example of a Codebreaker Shellcode log
json
{
"flow_id": "1288526885940394",
"@version": "1",
"timestamp_detected": "2021-07-01T09:30:57.781Z",
"SHA256": "1199e5d7281671962afaac9e6f36470f4f217b827ddbefa34026f509c025f76b",
"src_port": "27114",
"file_id": "07-01-2021T09:30:57_0431273753_gcap-int-ppo-164.domain.local",
"type": "codebreaker",
"@timestamp": "2021-07-01T09:31:03.666Z",
"event_type": "shellcode",
"calls": {
"0": {
"call": "kernel32_LoadLibraryA",
"args": "{'lpFileName': 'ws2_32'}",
"ret": 1880096768
},
"1": {
"call": "ws2_32_WSAStartup",
"args": "{'wVersionRequested': 400}",
"ret": 0
},
"2": {
"call": "ws2_32_WSASocketA",
"args": "{'af': 'AF_INET', 'type': 'SOCK_STREAM', 'protocol': 'IPPROTO_IP', 'g': 0, 'dwFlags': 0}",
"ret": 20
},
"3": {
"call": "ws2_32_connect",
"args": "{'s': 'Socket_1 (20)', 'name': '10.30.58.183:4444', 'namelen': 16}",
"ret": 0
},
"4": {
"call": "ws2_32_recv",
"args": "{'s': 'Socket_1-connected (20)', 'buf': '0x1237e5c', 'len': 4, 'flags': None}",
"ret": 4
},
"5": {
"call": "kernel32_VirtualAlloc",
"args": "{'lpAddress': 'Null', 'dwSize': '0xff', 'flAllocationType': 'MEM_COMMIT', 'flProtect': 'PAGE_EXECUTE_READWRITE'}",
"ret": 536870912
},
"6": {
"call": "ws2_32_recv",
"args": "{'s': 'Socket_1-connected (20)', 'buf': '0x20000000', 'len': 255, 'flags': None}",
"ret": 255
},
"stop": "End of shellcode"
},
"uuid": "1cfaba49-4f4b-4a25-b32a-1eb2ed8a8366",
"MD5": "aa9d9b771c61b9e2773f7b6b6d541d18",
"sub_type": "Windows_x86_32",
"severity": 1
"dest_ip": "31.28.224.101",
"timestamp_analyzed": "2021-07-01T09:31:03.666Z",
"encodings": [
{
"count": 33
"name": "Shikata_ga_nai"
}
],
"src_ip": "41.203.128.216",
"gcap": "gcap-int-ppo-164.domain.local",
"state": "Exploit",
"GCenter": "gcenter-int-ppo-237.domain.local",
"dest_port": "82"
}
3.1.2. Table summarising the Codebreaker Shellcode fields
| Fields | Required | Description | Values |
|---|---|---|---|
| MD5 | Yes | MD5 hash of the analysed file. | - |
| SHA256 | Yes | SHA256 hash of the analysed file. | - |
| calls.X.args | Yes | Arguments of the system call used. | - |
| calls.X.call | Yes | Name of the system call used. | - |
| calls.X.ret | Yes | Return code of the system call used. | - |
| calls.stop | Yes | Indicates the end of the shellcode system calls. | End of shellcode, End of shellcode (Exit) |
| dest_ip | Yes | Destination's IP address. | - |
| dest_port | Yes | Destination port. | - |
| encodings.count | Yes | Number of successive encodings. | - |
| encodings.name | Yes | Name of the encoding used. | - |
| event_type | Yes | Type of operation. | shellcode |
| file_id | Yes | File identifier. | - |
| file_id | Yes | Flow identifier. | - |
| gcap | Yes | Name of the gcap assigned to the alert. | - |
| gcenter | Yes | Name of the GCenter assigned to the alert. | - |
| severity | Yes | Severity level. | - |
| src_ip | Yes | Source IP address. | - |
| src_port | Yes | Port source. | - |
| state | Yes | Result of the codebreaker analysis. | Exploit, Suspicious |
| sub_type | Yes | The file's sub-type. The operating system linked to the executable if it is a shellcode. | Windows_x86_32, Linux_x86_32 |
| timestamp_analyzed | Yes | Date and time the file was last analysed. | - |
| timestamp_detected | Yes | Date and time of the file's first capture. | - |
| type | Yes | Type of event. | codebreaker |
3.2. Codebreaker Powershell
3.2.1. Codebreaker Powershell event modifications
3.2.2. Example of Codebreaker Powershell log
json
{
"flow_id": "2248143006711922",
"@version": "1",
"timestamp_detected": "2021-07-06T17:39:29.442Z",
"MD5": "c2eae0da7d9e27a10ae889cef2d21d0d",
"SHA256": "04fa65e0e344dfff0396ca9fe3e36ce55f1c2777c698874458b97289383e5de5",
"uuid": "340fb354-0439-495b-acad-104cb8bf2a31",
"sub_type": "powershell",
"severity": 1
"src_port": "55796",
"dest_ip": "10.127.0.222",
"type": "codebreaker",
"file_id": "07-06-2021T17:39:29_7620562351_gcap-int-ppo-164.domain.local",
"@timestamp": "2021-07-06T17:39:32.888Z",
"timestamp_analyzed": "2021-07-06T17:39:32.888Z",
"src_ip": "10.127.0.111",
"gcap": "gcap-int-ppo-164.domain.local",
"event_type": "powershell",
"state": "Exploit",
"scores": {
"proba_obfuscated": 1
"analysis": 134
"analysis_detailed": {
"WebClientInvokation": 0
"StrReplace": 10
"Base64": 0
"CharInt": 16
"StrCat": 12
"FmtStr": 96
"StrJoin": 0
}
},
"dest_port": "4242",
"gcenter": "gcenter-int-ppo-237.domain.local"
}
3.2.3. Table summarising the Codebreaker Powershell fields
| Fields | Required | Description | Values |
|---|---|---|---|
| MD5 | Yes | MD5 hash of the analysed file. | - |
| SHA256 | Yes | SHA256 hash of the analysed file. | - |
| dest_ip | Yes | Destination's IP address. | - |
| dest_port | Yes | Destination port. | - |
| event_type | Yes | Type of operation. | powershell |
| file_id | Yes | File identifier. | - |
| file_id | Yes | Flow identifier. | - |
| gcap | Yes | Name of the gcap assigned to the alert. | - |
| gcenter | Yes | Name of the GCenter assigned to the alert. | - |
| scores.analysis | Yes | Sum of the scores in the scores.analysis_detailed. fields*. | - |
| scores.analysis_detailed.Base64 | Yes | Score represented by an integer of one or more of the detected base64 patterns. | - |
| scores.analysis_detailed.CharInt | Yes | Score represented by an integer of one or more detected charint patterns. | - |
| scores.analysis_detailed.FmtStr | Yes | Score represented by an integer of one or more detected fmtstr patterns. | - |
| scores.analysis_detailed.StrJoin | Yes | Score represented by an integer of one or more detected strjoin patterns. | - |
| scores.analysis_detailed.StrReplace | Yes | Score represented by an integer of one or more detected strreplace patterns. | - |
| scores.analysis_detailed.WebClientInvokation | Yes | Score represented by an integer of one or more detected webclientinvokation patterns. | - |
| scores.proba_obfuscated | Yes | Probability of the powershell being attacked between 0 and 1. | - |
| severity | Yes | Severity level. | - |
| src_ip | Yes | Source IP address. | - |
| src_port | Yes | Port source. | - |
| state | Yes | Result of the codebreaker analysis. | Exploit, Suspicious |
| sub_type | Yes | The file's sub-type. | powershell |
| timestamp_analyzed | Yes | Date and time the file was last analysed. | - |
| timestamp_detected | Yes | Date and time of the file's first capture. | - |
| type | Yes | Type of event. | codebreaker |
4. GScan
4.1. Shellcode Scanning

Menu: Operators > GScan > Shellcode Scanning
GScan shellcode enables files to be manually submitted so that they can be analysed by the codebreaker detection engine.
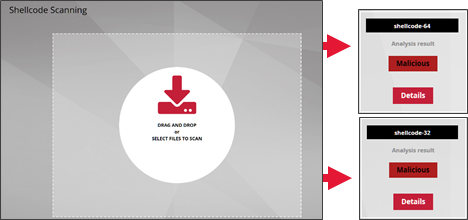
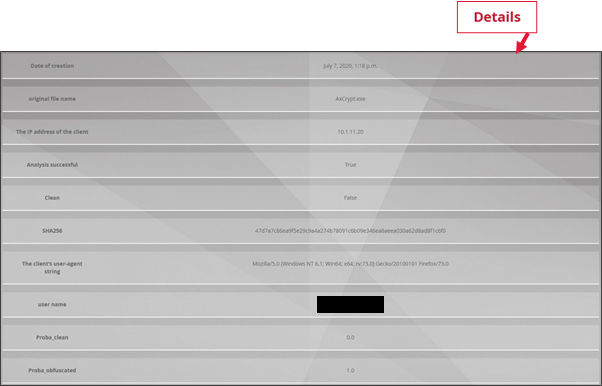
This information is available in the 'Details' section.
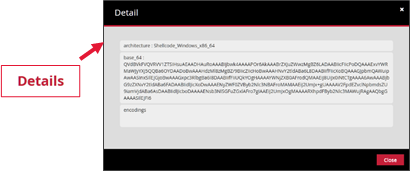
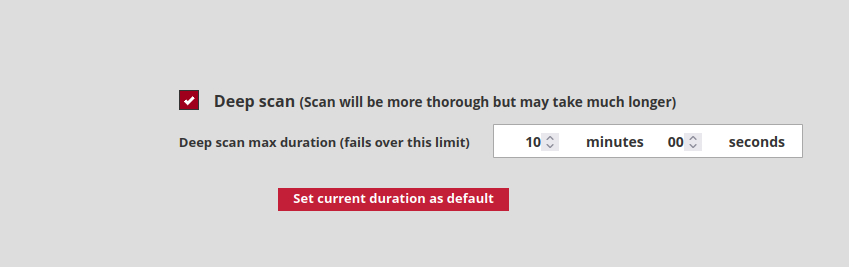
The Deep Scan function enables improved detection of unknown patterns or methods of obfuscation.
It is possible to configure the analysis time and to activate/deactivate the function.
4.2. Powershell Scanning


Menu: Operators > GScan > Powershell Scanning
This interface provides the ability to scan files containing POWERSHELL scripts and detect potential threats that can be used as an entry point to install malware on Windows.
As regards malicious powershells, detection is based on a supervised Machine Learning model, and on the fact that these scripts generally use obfuscation or similar techniques such as base64, concatenation, and type conversion, etc.
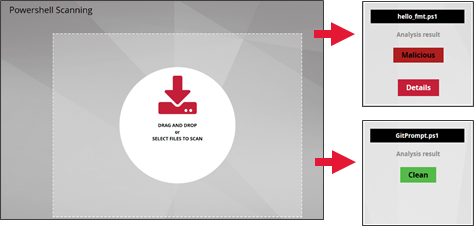
Some additional information is available under the 'Details' tab.
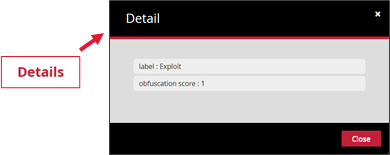
The result can be as follows: Clean or Malicious depending on the obfuscation score.
4.3. History

Menu:
Operators > GScan > Malware Scanning
Operators > GScan > Shellcode Scanning
Operators > GScan > Powershell Scanning
For all MALCORE, CODEBREAKER, and POWERSHELL scans, a history of analysed files per analysis engine is available.
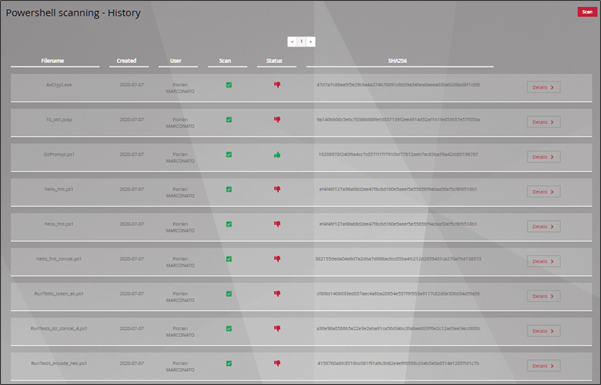
The list of files that have been analyzes can be seen on the interface.
Further information can be accessed via 'Details'.