1. Presentation
The MALCORE and RETROACT detection engines enable:
Detecting malware through a static and heuristic multi-engine analysis of files in real time.
Analysis via 16 Anti-Virus engines.
An analysis capacity of more than 6 million files per 24 hours.
Malware detection by re-analysing potentially harmful files after they pass through with new signatures and heuristic methods.
2. Configuration

Menu: Administrators > GCenter > Malcore Management
The MALCORE management interface enables modifying the GCENTER analysis parameters. From this section, the administrator is able to adjust the global detection parameters of the GCENTER:
2.1. Global settings

Menu: Administrators > GCenter > Malcore Management > Global Settings
The RETROACT analysis engine enables post-compromise detection by reanalysing, a posteriori, files whose malicious potential is suspected by MALCORE's heuristic analysis. These subsequent scans are performed over a configurable period of time, several days/weeks/months after the file has passed, with the new signatures and heuristic methods.
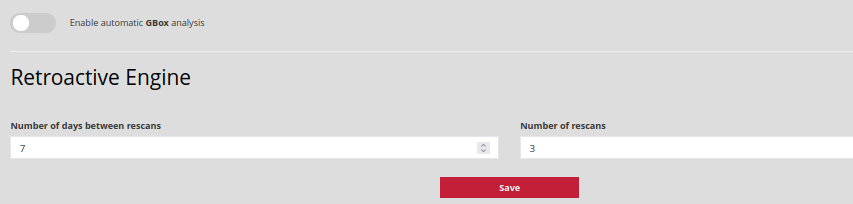
Number of days between rescans: This is the time period in days between each file rescan.
Number of rescans: corresponds to the amount of rescans to be performed.
For example, if Number of days between rescans is set to 3 and Number of rescans is set to 3, the suspicious file will be rescanned on D+3, D+6, and D+9.
Enable automatic GBOX analysis: allows the administrator to activate the automatic sending of all infected or suspicious files to the GBOX device if the link is operational.
2.2. Profiles

Menu: Administrators > GCenter > Malcore Management > Profiles
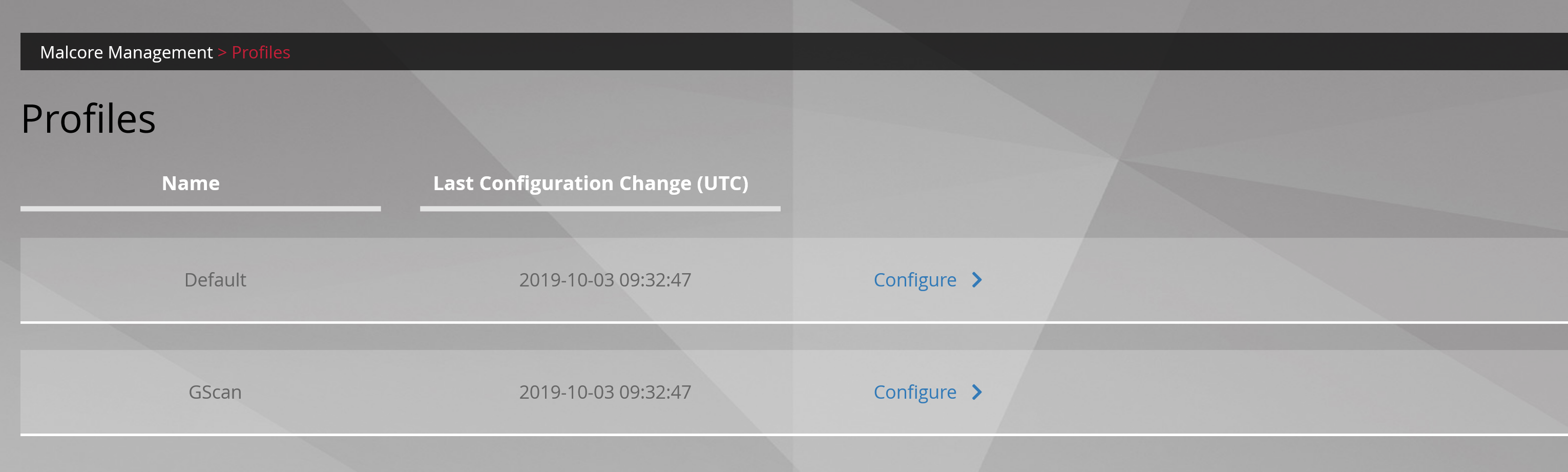
All MALCORE profiles are displayed in this view.
However, each profile can be modified as needed via the Configure button.
The Default profile will be used when processing files sent for analysis by gcaps.
The Gscan profile will be used for processing files submitted through the gscan interface.
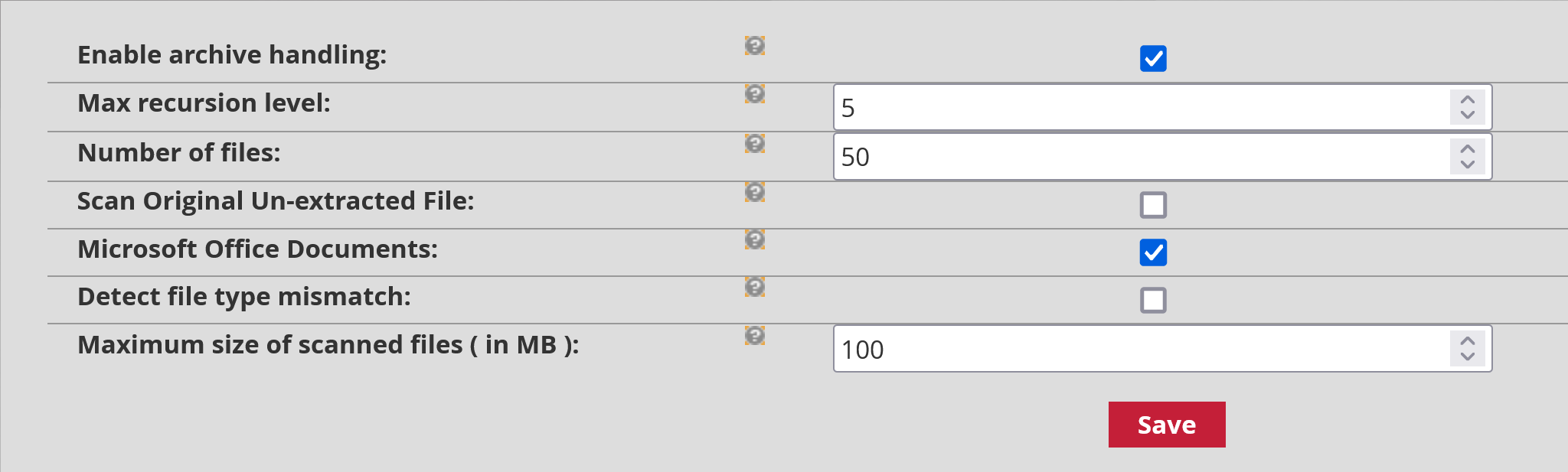
Enable archive handling: allows the scanning of all archive types by MALCORE (.zip, .rar, .upx).
Max recursion level: indicates the maximum depth level at which MALCORE will continue to scan files. For example, a .zip contains a folder that contains a folder that contains files. In this case, there are three levels of archive depth. If two is specified in the maximum possible recursion level, then all files in higher levels will not be scanned by MALCORE. Setting a limit here enables MALCORE to avoid overloading, though it will not scan all file levels. The default value is 5.
Number of files: this is the maximum number of files MALCORE can scan per archive. If this number is exceeded, then MALCORE will suspect something. The default number is 50 files.
Scan Original Un-extracted File: instructs MALCORE to consider the archive itself as a file.
Microsoft Office Documents: tells MALCORE to treat Office documents as Office documents (.docx, .xlsx) and not as an archive.
Detect file type mismatch: when ticked, if there is a mismatch between the file type and its extension, the file will appear as Mismatch in the dashboards in the GCENTER WEB interface.
Maximum size of scanned files (in MB): refers to the maximum size of files that are scanned by MALCORE.
Each of these items is taken into account after the administrator records the changes by pressing 'Save'.
2.3. Exception list

Menu: Administrators > GCenter > Malcore Management > White list / Black List
In the Malcore settings, it is possible to manage exception lists named Whitelist, for allowed hashes, and Blacklist, for prohibited hashes.
In the event a file to be analysed has a SHA256 hash present in the Blacklist, the result of the analysis will appear like this:
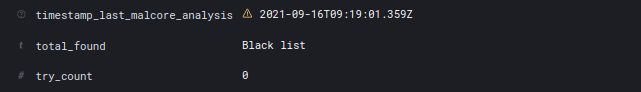
In the case of a Whitelist:
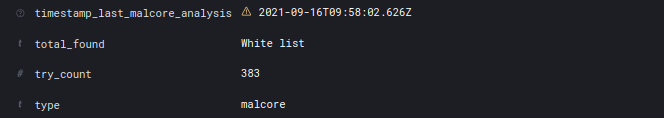
It is possible to add a hash to these lists either individually via the GCenter interface or by batch, by inserting a CSV file.

By clicking on Add a single file, a single hash can be added by filling in the Sha256 field and an optional remark for further details in the Comment field.
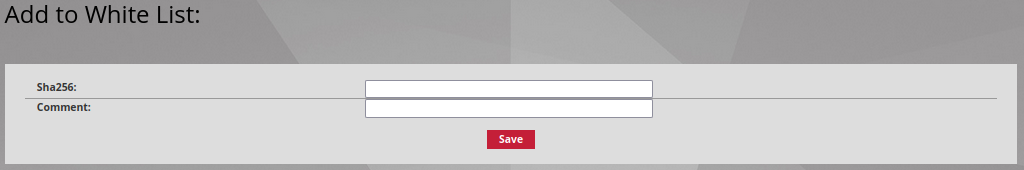
All of this information is taken into account after the administrator stores the changes by pressing Save.
By clicking on Add a set of files, by selecting a file in csv on their workstation, the administrator can add a list of hashes by clicking on the button in the List of SHA256 field. It is necessary to use ';' to separate the various elements of the list.
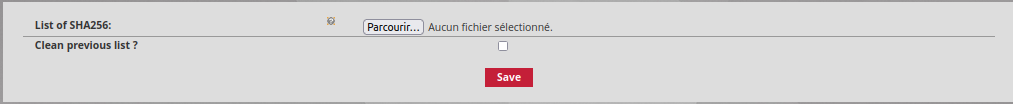
The administrator can decide to delete the previous list by ticking the Clean previous list? box and record all changes by clicking Save.
All additions and changes made from the White List and Black List sections of the MALCORE engine configuration settings will be taken into account in the analysis of the flow as well as for the files scanned via the GScan.
3. Detection
3.1. Inspectra
Menu: Operators > Inspectra > Malcore
From the 'OPERATORS - Inspectra - Malcore' section, the operator accesses a table listing the files seen as suspicious or infected through the MALCORE detection engine.
The RETROACT module will be tasked with highlighting suspicious files, if the feature is enabled.
The suspicious status is generated by the heuristic engines. These engines are able to detect abnormal elements. In the case of suspicious files, they will be reanalysed by RETROACT.
Suspicious files are detected by means of various antivirus engines, 1 in the CIE version and 16 in the other versions, operating in parallel. These engines were selected for their complementarity, the relevance of their common detection, their detection technology, and the origin of the security information used.
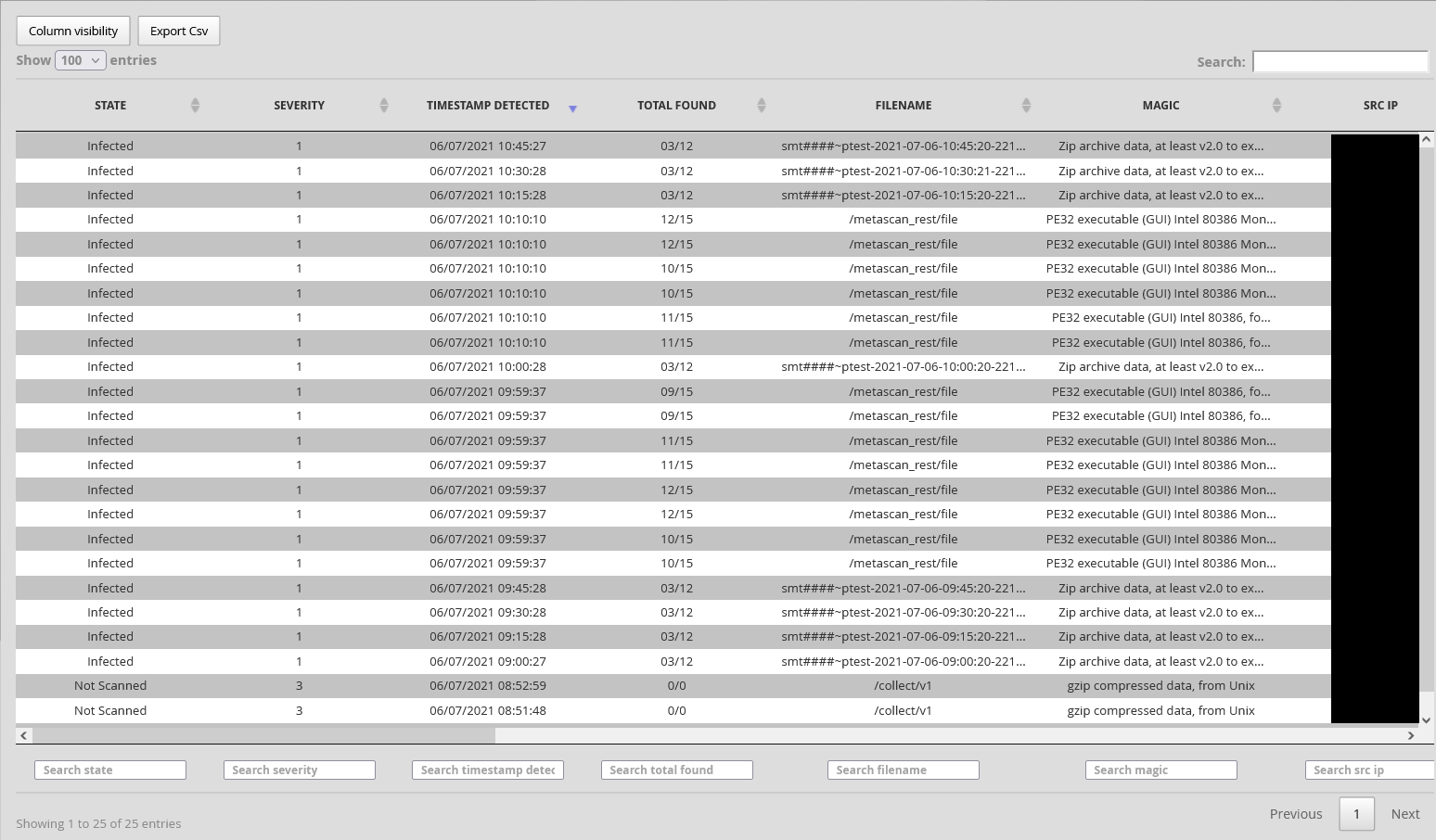
In the window above this table, the operator can click on the ' From - To' field to define the time range (in the format dd/mm/yyyy HH:MM) of the data being displayed.
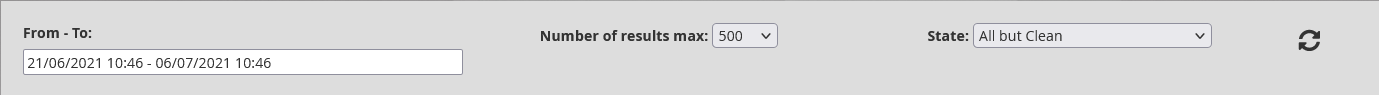
'Number of results max: is the maximum number of files (lines) displayed in the table.
The 'State' enables selecting the status of the alerts displayed according to the desired search.
| State | Description |
|---|---|
| All but Clean | All results, no threats. |
| All | All results, all threats. |
| Infected | Infected, known |
| Suspicious | Suspicious, listed as a possible threat but not identified as a specific threat. |
| Failed to Scan | scan not fully completed, e.g. invalid file or read not allowed. If no engine is included and analysis is enabled, this will be the final result. |
| Cleaned / Deleted | Cleaned, deleted. The threat was found and the file was repaired or deleted. |
| Unknown | Signature is not known, used in the multiple hash search. For single hash, scan responses are not reported. |
| Quarantined | The file is quarantined. |
| Skipped Clean | The analysis is ignored because this file type is whitelisted. |
| Skipped Dirty | The analysis is ignored because this type of file is blacklisted. |
| Exceeded Archive Depth | No threat detected although the archive level exceeds the threshold. The archive was not fully analysed. |
| Not Scanned / No scan results | No results, the analysis was ignored by the engines due to an engine update for a specific reason. If the analysis is disabled, this will be the final result. |
| Aborted | The current scan was stopped by the server |
| Encrypted | The file is not scanned because the file type is detected as encrypted and password protected. If the internal archive library is enabled, Malcore will not report any results as the engines are no longer scanning. If the internal archive library is disabled, Malcore will pass the encrypted files to the engines directly, bypassing detection. |
| Exceeded Archive Size | The size of the archive or file is too large to be analysed. |
| Exceeded Archive File Number | The number of files in the archive exceeds the configured number on the server. |
| Password Protected Document | Document secured by a password, e.g. Office or PDF documents requiring a password to view its contents. If a file is a password protected document, no disinfection will be performed. Malcore supports password protected document detection. Extensions for which detection operates PDF, DOCX, DOC, DOCM, DOTX, DOTM, POINT, PPTX, PPT, POT, POTM, POTX, PPS, PPSM, PPSX, PPTM, PPTX, XLSX, XLS, XLSM, XLSB, XLS, XLTX, XLTM, XLT, XLAM, XLA. |
| Mismatch | The file extension does not match the detected file type. Only applicable when dealing with workflows. |
| Potentially Vulnerable File | Possibly a susceptible file. |
The table's columns are movable and dynamic searches can be made on each of them:
The operator can choose the visibility of the columns in the table by clicking on the Column visibility button:
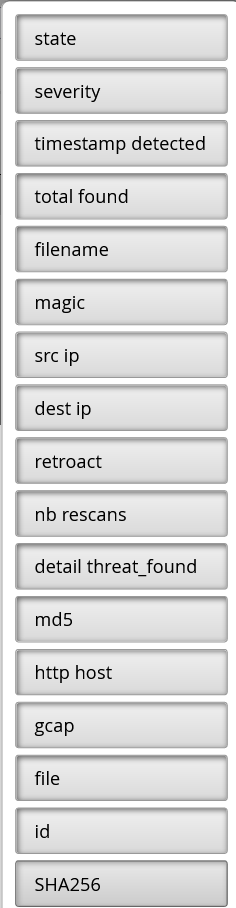
In addition, a vertical view of the alert is displayed via a right-click of the mouse.
A quick CSV export of the data based on the selected decision date:
An interactive analysis of the element is possible by means of a right click of the mouse. With 'Download malware' it is possible to retrieve the malware and save it on the computer in a password-protected file in `.zip' format. This password can be changed here.

The TRACKWATCH is able to provide further analysis of the detected malware through the Remote analysis' feature. If the configuration is completed beforehand, the operator can decide that the sample should be analysed in the https://intelligence.gatewatcher.com/ platform, i.e. a [GBOX] server (itg-ext/intelligence.html#gbox).

The analysis report generated by sending the infected file for further analysis can be downloaded using 'Download analysis report'.

The analysis parameters of the MALCORE engine can be changed in the default profile settings.
3.2. Dashboards

Menu: Operators > Dashboards > Malcore
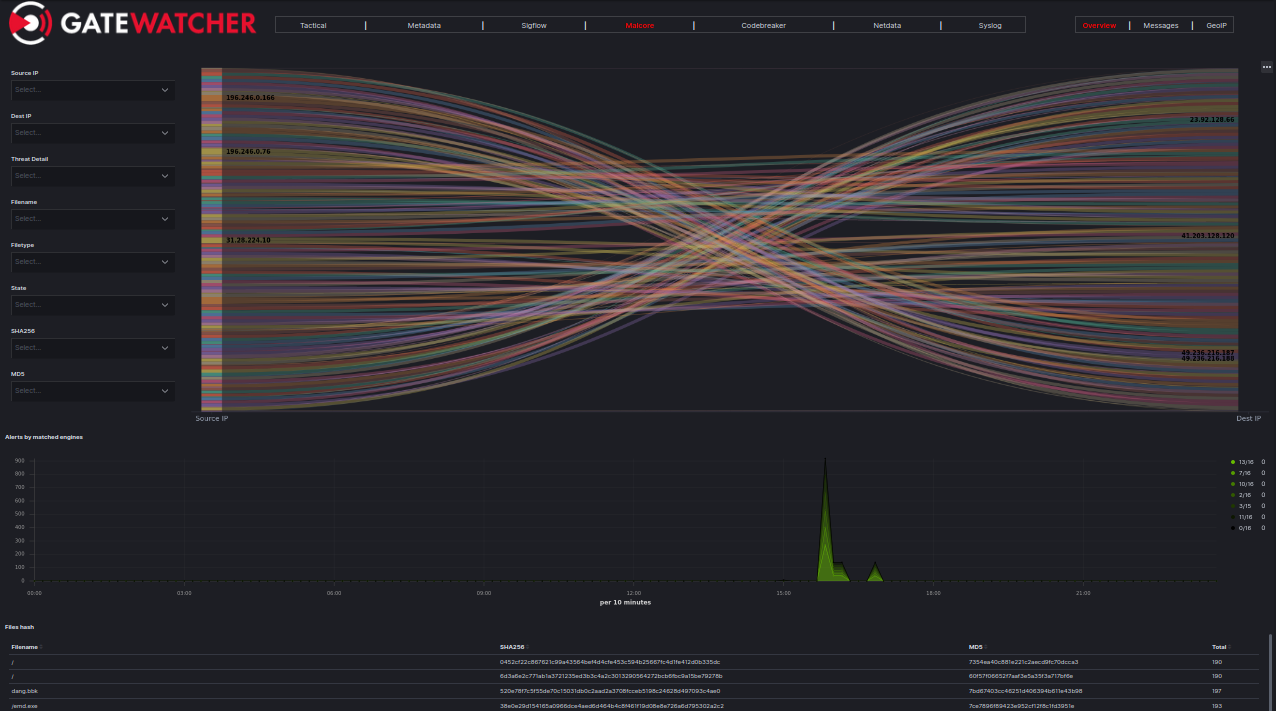
In addition to the information already included in the Inspectra table, the data collected by Malcore is also provided on the Malcore Kibana dashboard.
The data will be formatted as follows
4. Generated events
Attention
Engine ids are subject to change over time.
4.1. Example of a log
json
{
"engine_id": {
"714eca0a6475fe7d2bf9a24bcae343f657b230ff68acd544b019574f1392de77": "Trojan.Win32.Vebzenpak.iwgiuz",
"312a189607571ec2c7544636be405f10889e73d061e0ed77ca0eca97a470838d": "Gen:Variant.Graftor.961641",
"054a20c51cbe9d2cc7d6a237d6cd4e08ab1a67e170b371e632995766d3ba81af": "Trojan/Win.Generic",
"0ff95ddb1117d8f36124f6eac406dbbf9f17e3dd89f9bb1bd600f6ad834c25db": "Trojan.Multi",
"ecc47e2309be9838d6dc2c5157be1a840950e943f5aaca6637afca11516c3eaf": "W32/VBKrypt.AVU.gen!Eldorado",
"fe665976a02d03734c321007328109ab66823b260a8eea117d2ab49ee9dfd3f1": "Trojan.Win32.Injector",
"b14014e40c0e672e050ad9c210a68a5303ce7facabae9eb2ee07ddf97dc0da0e": "Trojan.Wacatac",
"527db072abcf877d4bdcd0e9e4ce12c5d769621aa65dd2f7697a3d67de6cc737": "Trojan.Vebzenpak.Win32.4817",
"32f2f45e6d9faf46e6954356a710208d412fac5181f6c641e34cb9956a133684": "a variant of Win32/Injector.EPML trojan",
"038e407ba285f0e01dd30c6e4f77ec19bad5ed3dc866a2904ae6bf46baa14b74": "Trojan.Agent (A)",
"4ca73ae4b92fd7ddcda418e6b70ced0481ac2d878c48e61b686d0c9573c331dc": "Trojan ( 0057dc101 )",
"3bfeb615a695c5ebaac5ade948ffae0c3cfec3787d4625e3abb27fa3c2867f53": "Trojan.Win32.Vebzenpak.afnw",
"af6868a2b87b3388a816e09d2b282629ccf883b763b3691368a27fbd6f6cd51a": "TR/Injector.vdnis",
"ad05e0dc742bcd6251af91bd07ef470c699d5aebbb2055520b07021b14d7380c": "TR/Injector.vdnis"
},
"@version": "1",
"detail_scan_time": 289
"timestamp_detected": "2021-07-05T18:14:45.354Z",
"SHA256": "9f07b7d90dc159c18619741bbbe05a2eb512a53865ba5101ba9f5668ec01c427",
"timestamp_last_malcore_analysis": "2021-07-05T18:15:35.546Z",
"file": "1198",
"detail_scan_result_i": 1
"retroact": "None",
"app_proto": "http",
"src_port": "80",
"type": "malcore",
"detail_wait_time": 88
"@timestamp": "2021-07-05T18:15:48.857Z",
"event_type": "malware",
"filename": "/Im/HBB.exe",
"total_found": "14/15",
"scans_history": [
{
"code": 1
"total_found": "14/15",
"timestamp_analyzed": "2021-07-05T18:15:35.542Z",
"state": "Infected"
}
],
"size": "110592",
"meta": "CLOSED",
"MD5": "31bbac78b447abc5a1138f5b0f3bb1ae",
"uuid": "857a9a3f-99e6-4b28-abdd-32a7c28f0295",
"magic": "PE32 executable (GUI) Intel 80386, for MS Windows",
"reporting_token": "",
"severity": 1
"detail_threat_found": "Infected: Trojan/Win.Generic, TR/Injector.vdnis, Gen:Variant.Graftor.961641, W32/VBKrypt.AVU.gen!Eldorado, a variant of Win32/Injector.EPML trojan, Trojan.Agent (A), Trojan.Win32.Injector, Trojan ( 0057dc101 ), Trojan.Win32.Vebzenpak.afnw, Trojan.Win32.Vebzenpak.iwgiuz, Trojan.Multi, Trojan.Wacatac, Trojan.Vebzenpak.Win32.4817",
"detail_def_time": "2021-06-23T00:43:00.000Z",
"nb_rescans": "Not reanalyzed",
"dest_ip": "10.7.0.15",
"replica": false,
"timestamp_analyzed": "2021-07-05T18:15:48.857Z",
"code": 1
"src_ip": "192.185.92.26",
"gcap": "gcap-int-ppo-164.domain.local",
"host": "gcap-int-ppo-164.domain.local",
"state": "Infected",
"GCenter": "gcenter-int-ppo-237.domain.local",
"dest_port": "54325",
"_internal_doc_id": "qPzhd3oBnng1PLWX9yKE",
"flow_id": 1191592708119283
"try_count": 0
}
4.2. Summary table of the fields
| Fields | Required | Description | Values |
|---|---|---|---|
| MD5 | Yes | MD5 hash of the analysed file. | - |
| SHA256 | Yes | SHA256 hash of the analysed file. | - |
| app_proto | Yes | Application protocol of the flow from which the file originates. | http, ftp, smtp, smb |
| code | Yes | Return code from the malcore analysis. | 0, 1, 2, 3, 7, 8, 9, 10, 12, 13, 14, 16, 17, 18, 255 |
| dest_ip | Yes | Destination's IP address. | - |
| dest_port | Yes | Destination port. | - |
| detail_def_time | No | Date of updating the malcore signature database. This field must appear for all analyses | - |
| detail_scan_result_i | No | Return code from the malcore analysis. | 0, 1, 2, 3, 7, 8, 9, 10, 12, 13, 14, 16, 17, 18, 255 |
| detail_scan_time | No | File analysis time (ms) by malcore engines. | - |
| detail_threat_found | Yes | Type of threat. | - |
| engine_id | No | List of malcore engines having analysed the file with the corresponding result. | - |
| event_type | Yes | Type of event. | malware |
| file | Yes | File identifier. | - |
| fileinfo_potentially_involved | No | This field only appears in the case of retroact - it shows the list of doc _id less than 24 hours old that are affected by the rescan. | - |
| filename | Yes | File name. | - |
| flow_id | No | Unique flow identifier. Enables retrieving the associated fileinfo. | - |
| gcap | Yes | Name of the gcap assigned to the alert. | - |
| gcenter | Yes | Name of the GCenter assigned to the alert. | - |
| host | Yes | Name of the gcap assigned to the alert. | - |
| magic | yes | Type of payload. | - |
| nb_rescans | Yes | Number of analyses per retroact | "Not reanalyzed", 1, 2 .. n |
| replica | Yes | Field is False if the file is being viewed for the first time and True if it is a replica. | True, False |
| reporting_token | Yes | Token used with the Gbox. | - |
| retroact | Yes | Result of the retroact analysis By default this field is set to NONE. Only suspicious files will be re-scanned by retroact. | This field can be set to None or advanced malware, if retroact declares the file as infected |
| severity | Yes | Code for the result of the malcore analysis. Must be between 0 and 3. | 0=clean, 1=infected, 2=suspicious, 3=Other |
| size | Yes | File size. | - |
| src_ip | Yes | Source IP address. | - |
| src_port | Yes | Port source. | - |
| state | Yes | Result of the analysis by the malcore engines. | No Threat Detected Infected Suspicious Failed Scan Skipped - Whitelisted Scan Skipped – Blacklisted Not Scanned Exceeded Archive Depth Encrypted Archive Exceeded Archive Size Exceeded Archive File Number Exceeded Archive Timeout Filetype Mismatch Potentially Vulnerable File In Progress 0 in the case of a whitelisted file 1 in the case of a blacklisted file |
| timestamp_analyzed | Yes | Timestamp of the alert processing by the GCenter corresponds to the passage in logstash | - |
| timestamp_detected | Yes | Timestamp of the file capture by gcap | - |
| timestamp_last_malcore_analysis | Yes | Timestamp of the file's last scan by malcore. Replicas are not reanalysed, so the "timestamp_last_malcore_analysis" may be older than the "timestamp_analyzed" | - |
| total_found | Yes | Number of engines detecting the file as infected. | XX/YY with YY between 0 and 16 and XX between 0 and YY. YY=number of engines that analysed the file. XX: number of engines whose result was different from "clean". - "File size exceeded the maximum size" if the file was too big to be analysed by malcore. (See Administrators > malcore management > profile > Default > Maximum size of scanned files) - "Black list", or "White list" in the case of malcore blacklist/whitelist (See Administrators > malcore management > whitelist/blacklist) |
| try_count | No | Attempts to enrich. Internal field for GCenter operation | - |
| type | Yes | Type of event. | malcore |
| detail_wait_time | No | wait_time: time elapsed between sending file to node and receiving the result from the engine in milliseconds | - |
| meta | Yes | Completeness of the analysed file (CLOSED) otherwise TRUNCATED. | CLOSED, TRUNCATED |
| scan_time_average | No | File analysis time (ms) by malcore engines. This field should appear systematically | - |
| scans_history.code | Yes | Code for the result of the malcore analysis. | 0, 1, 2, 3, 7, 8, 9, 10, 12, 13, 14, 16, 17, 18, 255 |
| scans_history.state | Yes | Result of the analysis by the malcore engines. | No Threat Detected Infected Suspicious Failed Scan Skipped - Whitelisted Scan Skipped – Blacklisted Not Scanned Exceeded Archive Depth Encrypted Archive Exceeded Archive Size Exceeded Archive File Number Exceeded Archive Timeout Filetype Mismatch Potentially Vulnerable File In Progress |
| scans_history.timestamp_analyzed | Yes | Timestamp of the file analysis. | - |
| scans_history.total_found | Yes | Number of engines detecting the file as infected. | same as total_found |
| _internal_doc_id | No | Field used for Gcenter's internal operation | _id de documents elasticsearch |
The syslog export has additional fields:
smtp.mail_from,
smtp.rcpt_to,
email.from, email.to,
email.cc,
email.bcc,
email.in_reply_to,
http.hostname,
http.url,
http.http_refer,
http.http_user_agent.
Warning
These fields are affected by a known bug (see release note.)
Warning
The enrichment at the origin of these fields will be depreciated in v2.5.3.102.
5. Detection by gscan

Menu: Operators > GScan > Malware Scanning
Note
When deployed in an MPL environment, GScan functionality is disabled
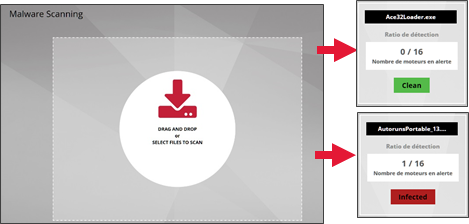
Gscan enables an operator to submit a file via the GCenter web interface for malcore analysis
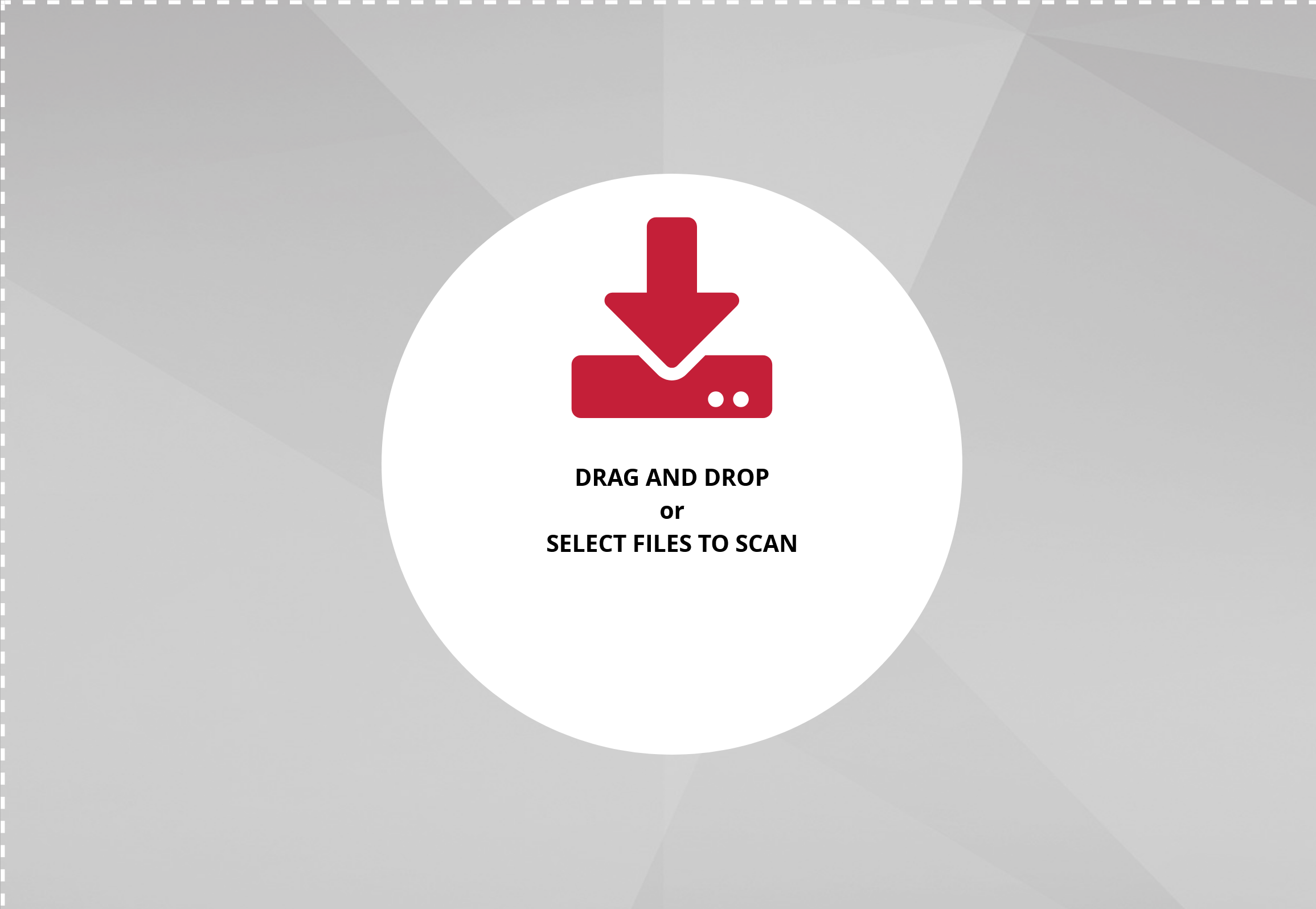
To start analysing a file, simply drag it into the DRAG and DROP or SELECT FILES TO SCAN area or click on this area to send your suspicious executables.
Please note that the maximum file size must not exceed 10MB. There is no limit to the number of file scans. The scan result shows almost instantly the status of the sample after analysis. The result can be as follows: Clean or Infected across the 16 engines.