7.5.11. Analyzing the Yara alerts
7.5.11.1. Introduction
For information, see the following paragraphs:
7.5.11.1.1. Management of the Yara engine
7.5.11.1.2. Events generated by the engine
- In the main interface named WebUI of the GCenter in the
`Alerts`screen:The main interface named WebUI is described in Overview of the WEB UI.To filter the Yara alerts, type
`name:"Yara Rule Matched"`in the search field then validate.- Use the
`Group by name`selector to view the number of different alerts.The name of the aggregated alerts and their numbers are displayed.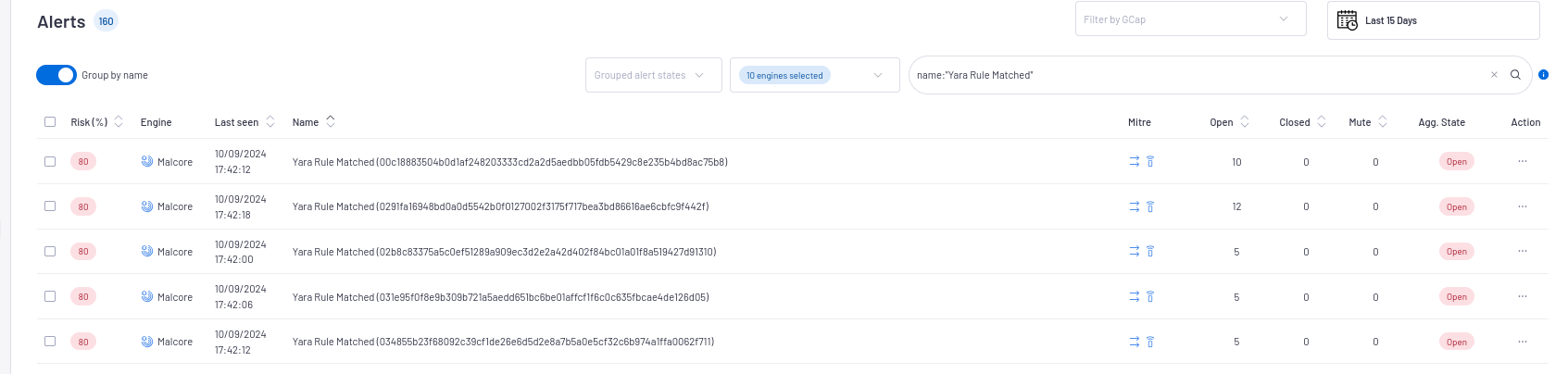
Click on a grouping of alerts to display the list, if needed.
- Disable the
`Group by name`selector.Different Source and Destination information is displayed for each alert.`Tags`and`Notes`are also visible and editable.The various Quick Access`Actions`are available for each alert. - Click on an alert.The detailed information of this alert is displayed in Example of an Yara alert in the WebUI.
- In the Kibana UI interface
To view all Yara alerts:
- In the main interface WebUI, click on the
`Hunting`icon.The main interface named WebUI is described in Overview of the WEB UI. Click on the
`Malcore`tab (2) of the`Alerts`category (1).Select the
`Overview`tab (3).- Select the time range (4) to display data.See the presentation of the WebUI `Alerts` screen.
To filter the Yara alerts on Kibana, enter the following command
`event.module : "malcore" and malcore.state : "Yara Rule Matched"`(5) in the search field.Validate wih the
`Refresh`button (6).
To consult information about a specific alert:
- After selecting the alert, click on the
`Open malcore file transaction`command of the`Actions`menu.Kibana is opened on the`Malcore`tab of the`Alerts `section: in the`Overview`tab, the database is filtered on the`file.hash.sha256`parameter (7).The interface displayed is the interface named Kibana UI (described in Overview of the Kibana GUI).
Click on the
`Messages`tab (8).- Click on the toggle icon (9) on the left of the AlertThe expanded document is displayed.The detailed information of this alert can be viewed in table or json format (see the Yara log data structure).The displayed counters are given in the Engine log data structure appendix.
Note
The Kibana UI can also be accessed without any filters via the
`Hunting`icon on the left side menu bar in the WebUI.
7.5.11.1.3. Essential information to understand the context of the alert
7.5.11.1.3.1. What are the key fields of an alert and their meaning?
In the information displayed on the WebUI `Alerts` screen, these key elements include:
`Engine:`The alerts related to the Yara engine include the term`Malcore`for the Engine field.`Date:`The date when the engine rose an alert in the local timezone. The UTC date is accessible in the alert detail under .event.created`Name:`At the beginning of this field is indicated the result of the Yara scan (yara rule matched) associated to the the sha256 of the file.`Src. IP`and`Dest. IP`The IP addresses associated with the alert, whether source or destination, provide information about the network communication involved in the incident.`Src. Host.`and`Dest.Host.`The source and destination hosts associated with the alert provide information about the systems involved in the network communication of the incident.
More information is available on the `Alert Details` screen after clicking on an alert in the `Alerts` screen of the WebUI.
Click on the
`Details`tab (1).`detail_threat_found`: this field is always`yara rule matched``protocol`This field indicates the protocol through which the file was observed on the network.This information can help identify how the file was delivered or offer a way to gather more protocol-specific information.`magic details`This is the file format detected by Malcore.The file format is not detected based on filename or extension but rather by the content of the file.This information can help to understand the nature of the malicious file in question, in particular the platforms that are targeted and it sometimes allow to reveal the real nature of a file.For example: "PE32 executable (GUI) Intel 80386, for MS Windows".In this example, "PE32 executable" indicates that it is an executable file in Portable Executable format, commonly used for Windows programs.`file.name`This field indicates original filename used during the delivery.`file.hash.md5`and`file.hash.sha256`These fields indicate the checksum respectively in MD5 and SHA256 of the sample.This checksum is a unique value representing the content of a file.
7.5.11.2. Alert handling procedure
7.5.11.2.1. How do you verify the accuracy of an alert and determine if it represents a real threat?
7.5.11.2.2. What answers are needed if the threat is confirmed?
Note
This procedure allows to deepen the investigation and assess the extent of the incident after confirmation of a threat generated by the Yara engine
Isolate the system: immediately isolate the contaminated system and ensure it cannot cause further damage
Notify: inform relevant parties of threat detection
Dynamic analysis: if possible, run the file in a secure environment (sandbox) to observe its behavior (a GBox for example)
Collect information: gather essential information such as file hash, file name, source and location
Neutralize the threat by deleting the file, blocking the original IP address, etc.
- Reverse engineering (if necessary): if the threat is particularly complex, reverse engineering can be considered to understand in depth its internal functioning.This can help identify exploited vulnerabilities and propagation mechanisms.The feature
`Download Malware`, presented previously, enables to recover the file for analysis. Analyze logs: review system and network logs to trace the spread of the threat.